Snyk Container is a developer-focused container vulnerability management tool that scans images and Kubernetes configurations for security issues. Part of the Snyk platform, it analyzes application dependencies and operating system packages to identify vulnerabilities, malware, and licensing risks in containerized applications.
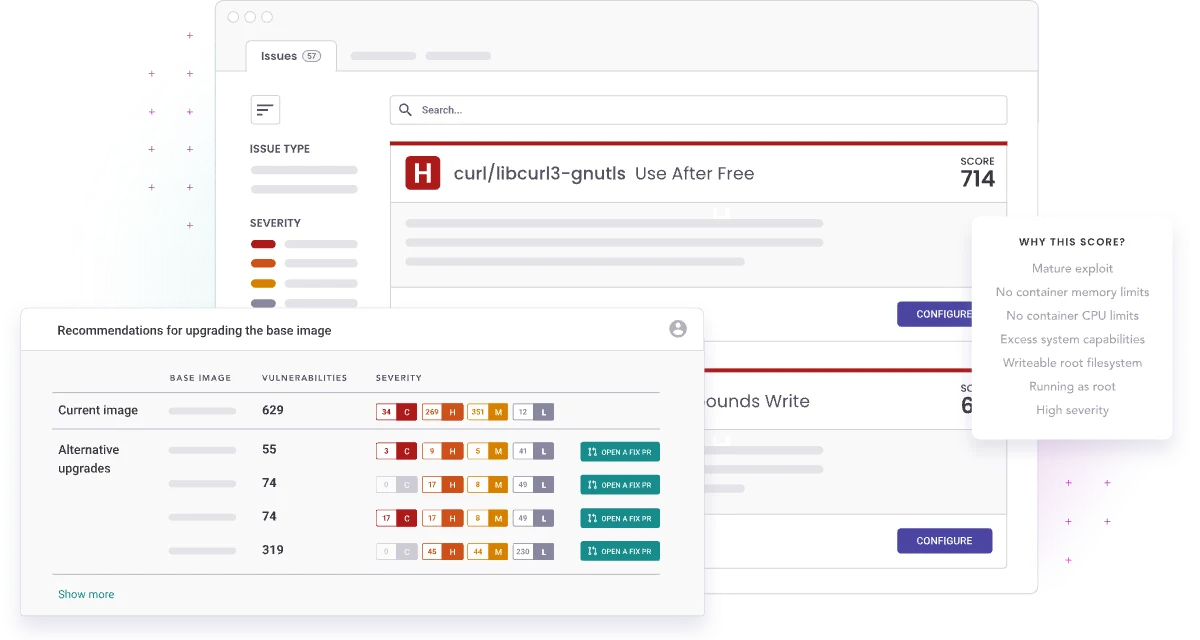
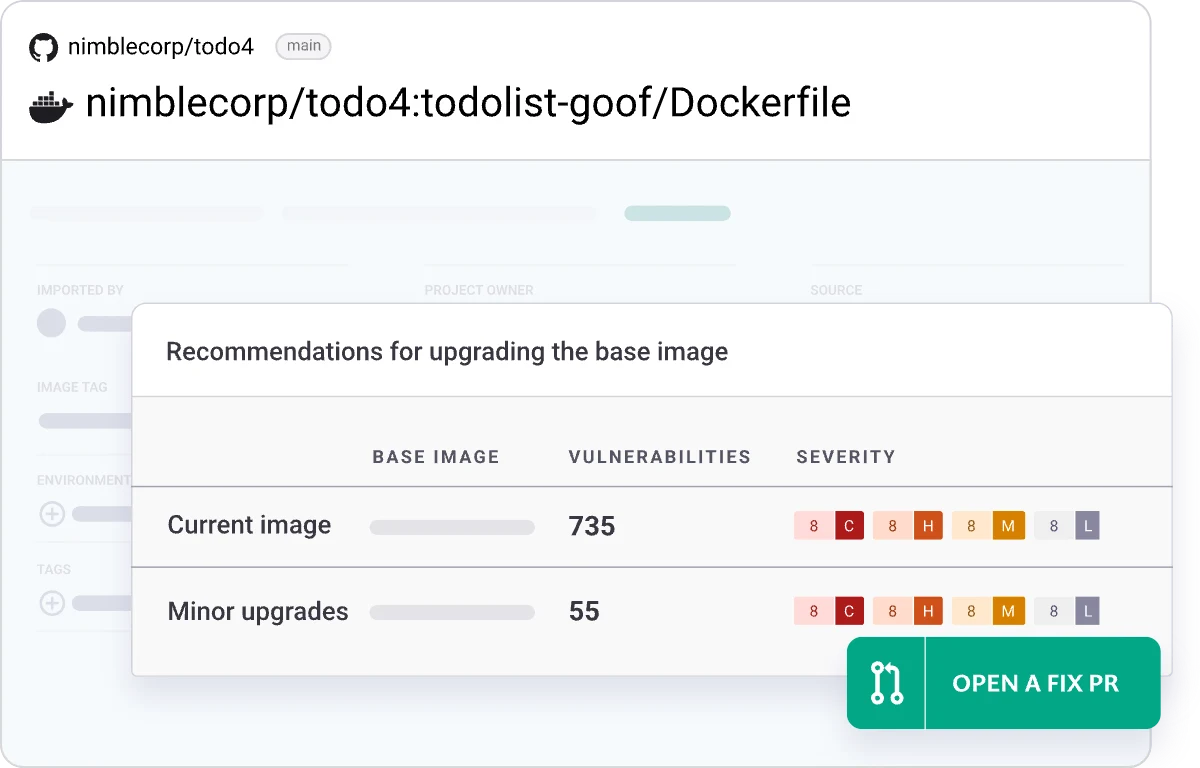
The tool provides actionable remediation guidance directly in development workflows. Instead of listing CVEs without context, Snyk Container recommends specific base image upgrades that resolve issues with minimal changes.
What is Snyk Container?
Snyk Container scans both the application layer and base OS layer of container images. It identifies vulnerabilities in language-specific dependencies (npm, pip, Maven) as well as operating system packages installed via apt, yum, or apk.
When vulnerabilities are found in the OS layer, Snyk recommends specific alternative base images or versions that resolve the issues. If your app uses node:16 with vulnerabilities, Snyk might suggest node:16-alpine as a smaller image with fewer vulnerabilities.
Kubernetes manifest scanning extends beyond images to identify configuration issues: containers running as root, missing resource limits, exposed secrets, and violations of pod security standards.
Key features
| Feature | Details |
|---|---|
| Image scanning | Application dependencies + OS packages across all image layers |
| Base image recommendations | Specific upgrade paths with vulnerability count comparison |
| Runtime insights | Production container data for exploitability prioritization |
| Container registries | Docker Hub, ECR, ACR, GCR, Artifactory, Harbor, Quay |
| Kubernetes platforms | EKS, AKS, GKE, OpenShift, Tanzu |
| Malware detection | Supply chain attack detection in base images and dependencies |
| License compliance | Policy-based blocking of images with problematic licenses |
| Pricing | Free (community), Team (Jira integration), Enterprise (full features) |
Registry integration
Snyk Container connects to container registries and scans images automatically as they are pushed. This continuous monitoring catches new vulnerabilities as they are disclosed, alerting teams to risks in deployed images without manual rescans.
Kubernetes monitoring
Deploy the Snyk Controller to continuously monitor workloads across EKS, AKS, GKE, OpenShift, and Tanzu. The controller detects vulnerabilities and misconfigurations in running pods.
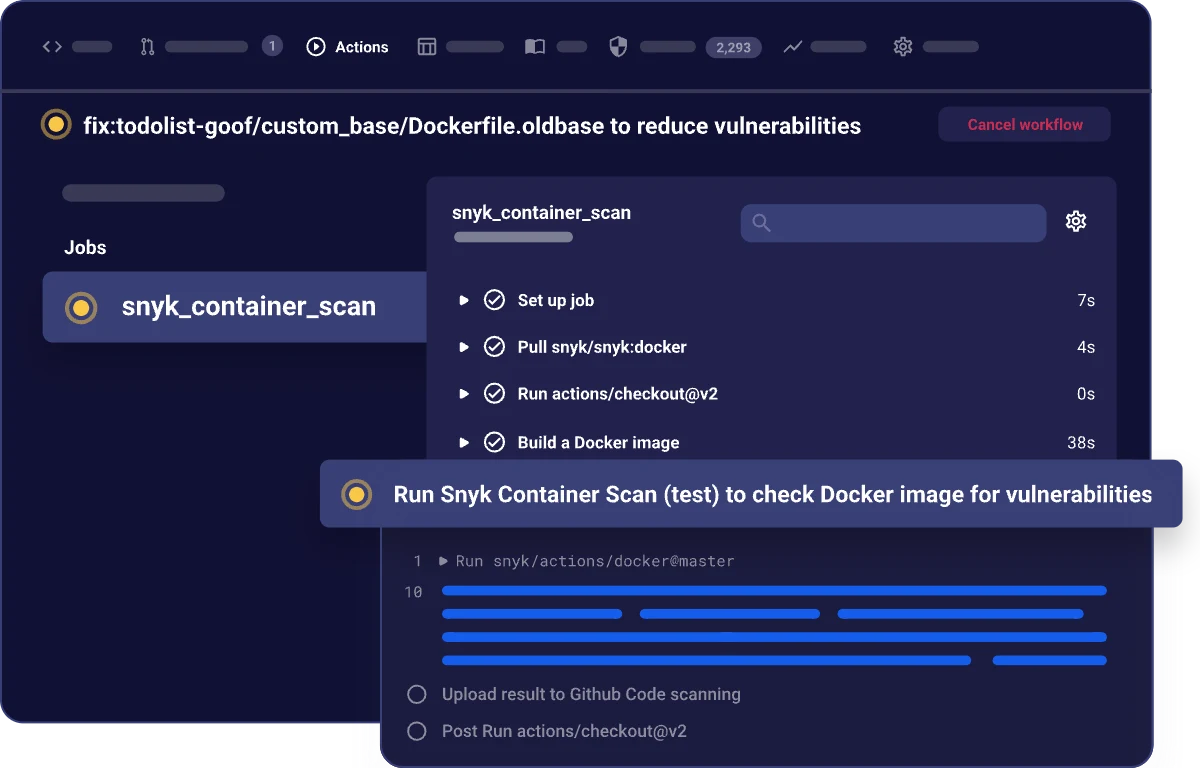
CI/CD integration
Plugins for Jenkins, GitHub Actions, GitLab CI, and CircleCI fail builds when critical vulnerabilities are found, preventing insecure images from being deployed.
IDE support
Developers can scan Dockerfiles directly in VS Code, IntelliJ, and other IDEs. This feedback helps pick secure base images and dependencies before committing code.
Integrations
Getting started
snyk container test nginx:latest via CLI, or let the registry integration scan images on push.When to use Snyk Container
Snyk Container fits development teams building containerized applications who want vulnerability scanning integrated into their existing workflows. The base image recommendations are the standout feature: instead of a CVE list, you get actionable upgrade paths.
The free tier suits individual developers and small projects. Enterprise teams benefit from Kubernetes monitoring, self-hosted registry support, and runtime insights.
For runtime threat detection (not just scanning), consider pairing with tools like Falco. For admission control to enforce image policies at deploy time, look at Kyverno.
Snyk Container fits into a broader SCA tools strategy by focusing specifically on containers. Teams often combine it with Snyk Open Source for dependency scanning and Snyk IaC for infrastructure configuration checks.
Further reading: Container Image Security | What is SCA? | Software Supply Chain Security