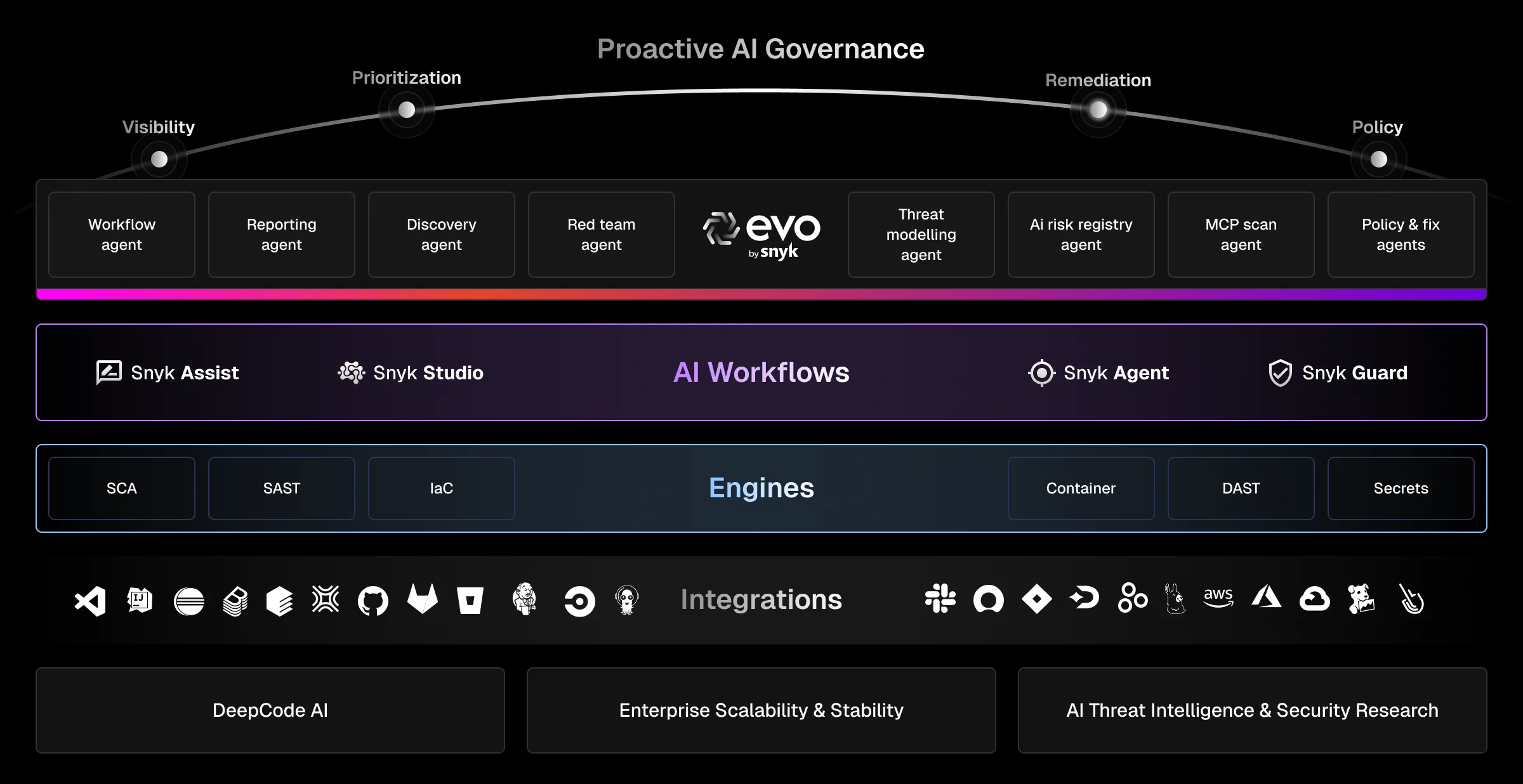
Snyk is a developer security platform that combines SCA, SAST, container scanning, IaC security, and DAST into a single product. It integrates into IDEs, Git repositories, CI/CD pipelines, and container registries.
The platform includes six products: Snyk Code (SAST), Snyk Open Source (SCA), Snyk Container, Snyk IaC, Snyk API & Web (DAST), and Snyk Studio for AI-generated code. All share a unified dashboard and security policy engine.
Snyk is recognized in the Gartner Magic Quadrant for Application Security Testing and named a Forrester Wave Leader in 2024. Customers include Twilio, Snowflake, Spotify, Revolut, and Komatsu.
What is Snyk?
Snyk covers cloud-native application security from a single platform. The company reports 288% ROI from consolidated solutions, 80% faster scan time than prior tools, and 75% faster remediation in upstream development.
Purpose-built AI engine with 25M+ data flow cases modeled. Generates context-aware fixes with 80% accuracy.
Not a general-purpose LLM — built specifically for security analysis.
Key features
| Feature | Details |
|---|---|
| Snyk Code (SAST) | Semantic analysis with data flow tracking, AI fix suggestions, 16 languages, 50x faster than legacy SAST |
| Snyk Open Source (SCA) | Dependency scanning, automated fix PRs, license compliance, reachability analysis, 24k+ new vulns discovered in 2024 |
| Snyk Container | OS package vulnerabilities, base image recommendations, registry integration |
| Snyk IaC | Terraform, CloudFormation, Kubernetes, Helm, ARM template scanning with CIS benchmarks |
| Snyk API & Web (DAST) | Dynamic application and API security testing |
| Snyk Studio | Security scanning for AI-generated code, covers 90% of LLM libraries including OpenAI and Hugging Face |
| Language support | Apex, C/C++, Dart/Flutter, Elixir, Go, Groovy, Java, Kotlin, JavaScript, TypeScript, .NET, PHP, Python, Ruby, Rust, Scala, Swift/Objective-C |
| SCA ecosystems | npm, Maven, Gradle, pip, Go modules, NuGet, RubyGems, Composer, Cocoapods, Cargo, Hex |
| Performance | 288% ROI, 80% faster scan time, 75% faster upstream remediation, 52% reduced data breach risk |
Snyk Code (SAST)
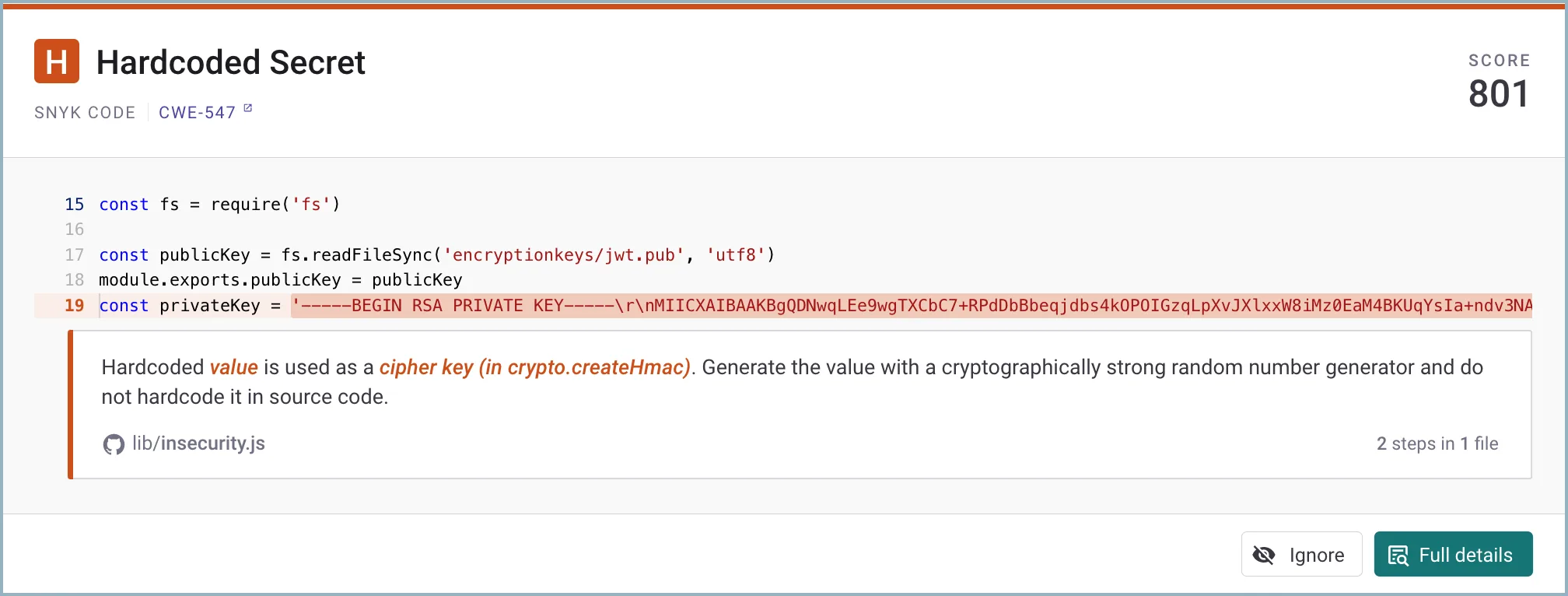
Snyk Code scans source code for security issues like SQL injection, XSS, command injection, path traversal, and insecure authentication. The semantic analysis engine traces data flow through code to detect vulnerabilities that span multiple files.
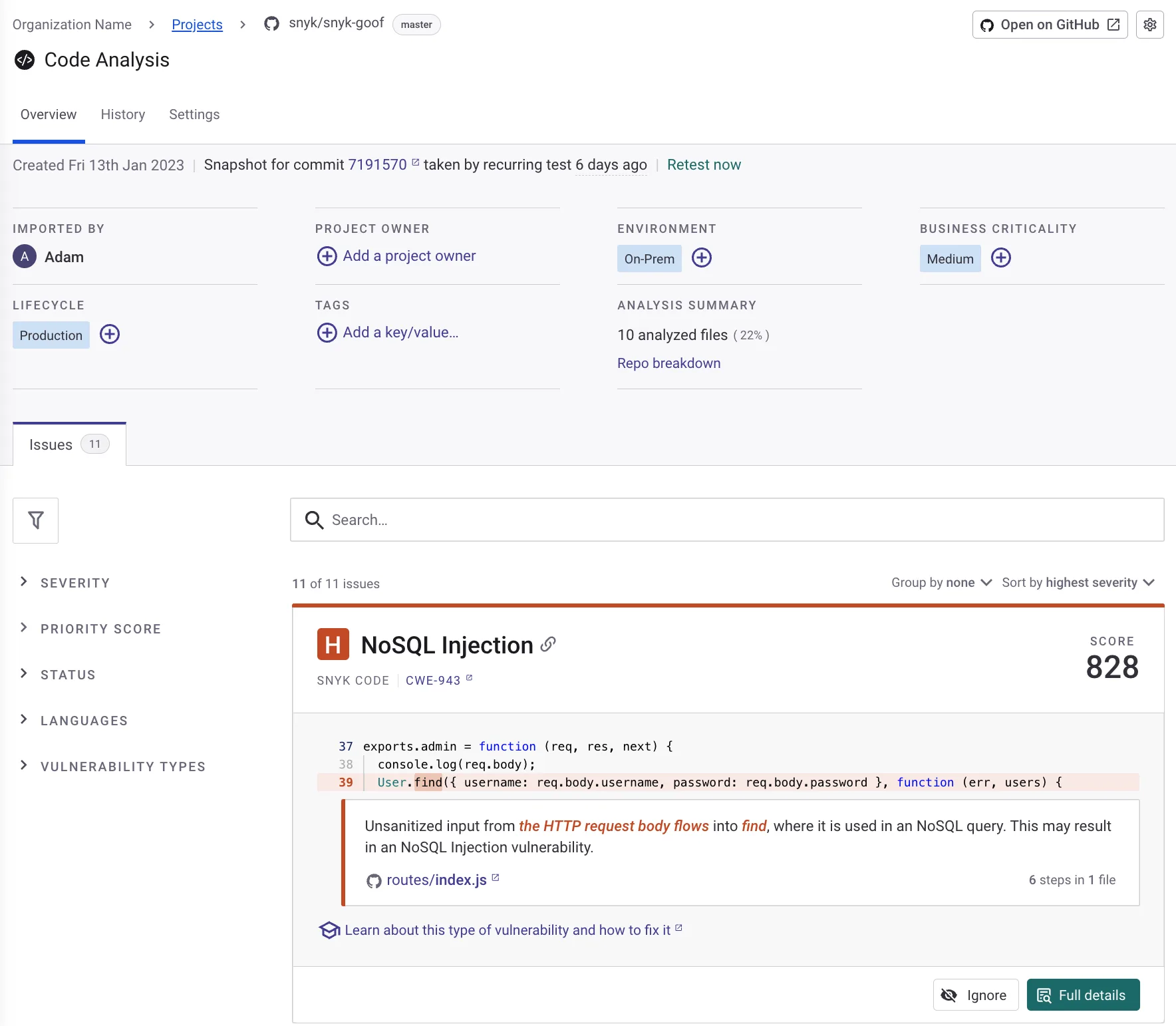
Snyk claims scans run 50x faster than legacy SAST tools and 2.4x faster than other modern SAST tools. No compilation or build step required.
DeepCode AI generates context-aware fix suggestions. Snyk reports 80% fix accuracy and an 84% reduction in mean time to remediate.
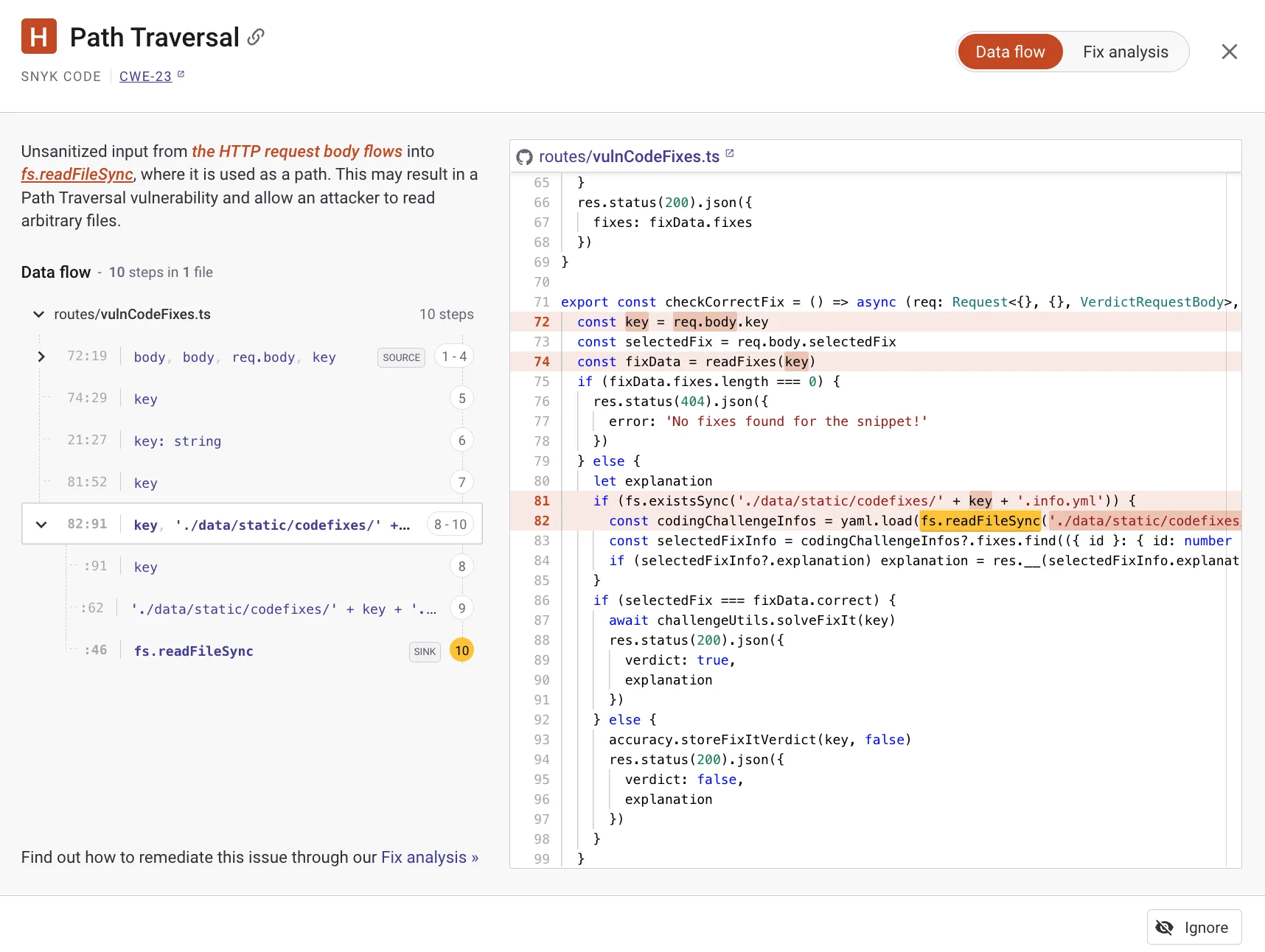
The data flow view shows exactly how tainted input travels through your code from source to sink. This makes it easier to understand why a finding is flagged and where to apply the fix.
Fix analysis
When Snyk Code detects a vulnerability, the fix analysis view shows what needs to change and why. For supported issues, DeepCode AI generates a specific code fix you can apply directly.
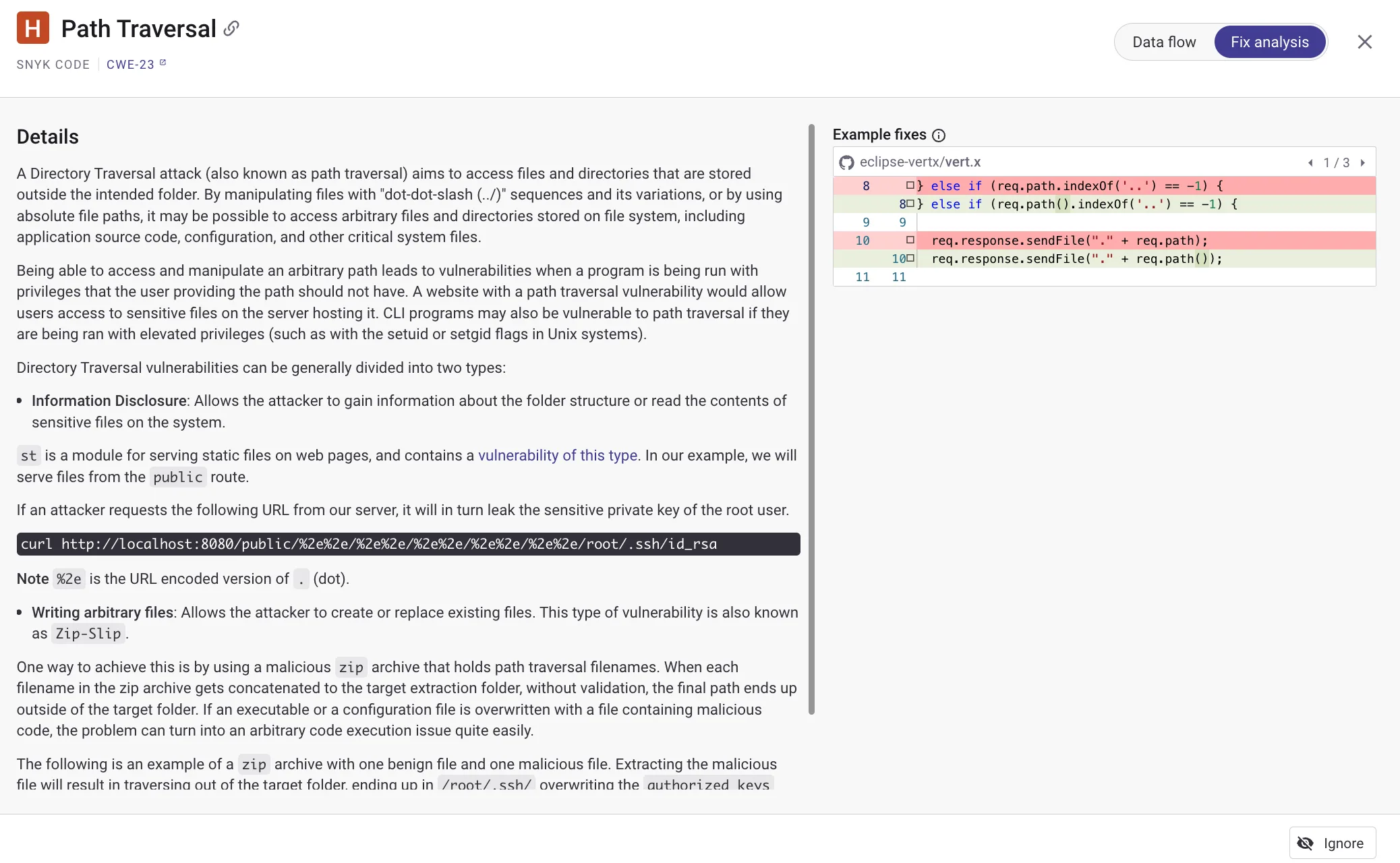
Automated fix pull requests work for both SAST and SCA findings. For dependencies, Snyk opens PRs with the required upgrades and patches. You can customize PR templates.
Snyk Open Source (SCA)
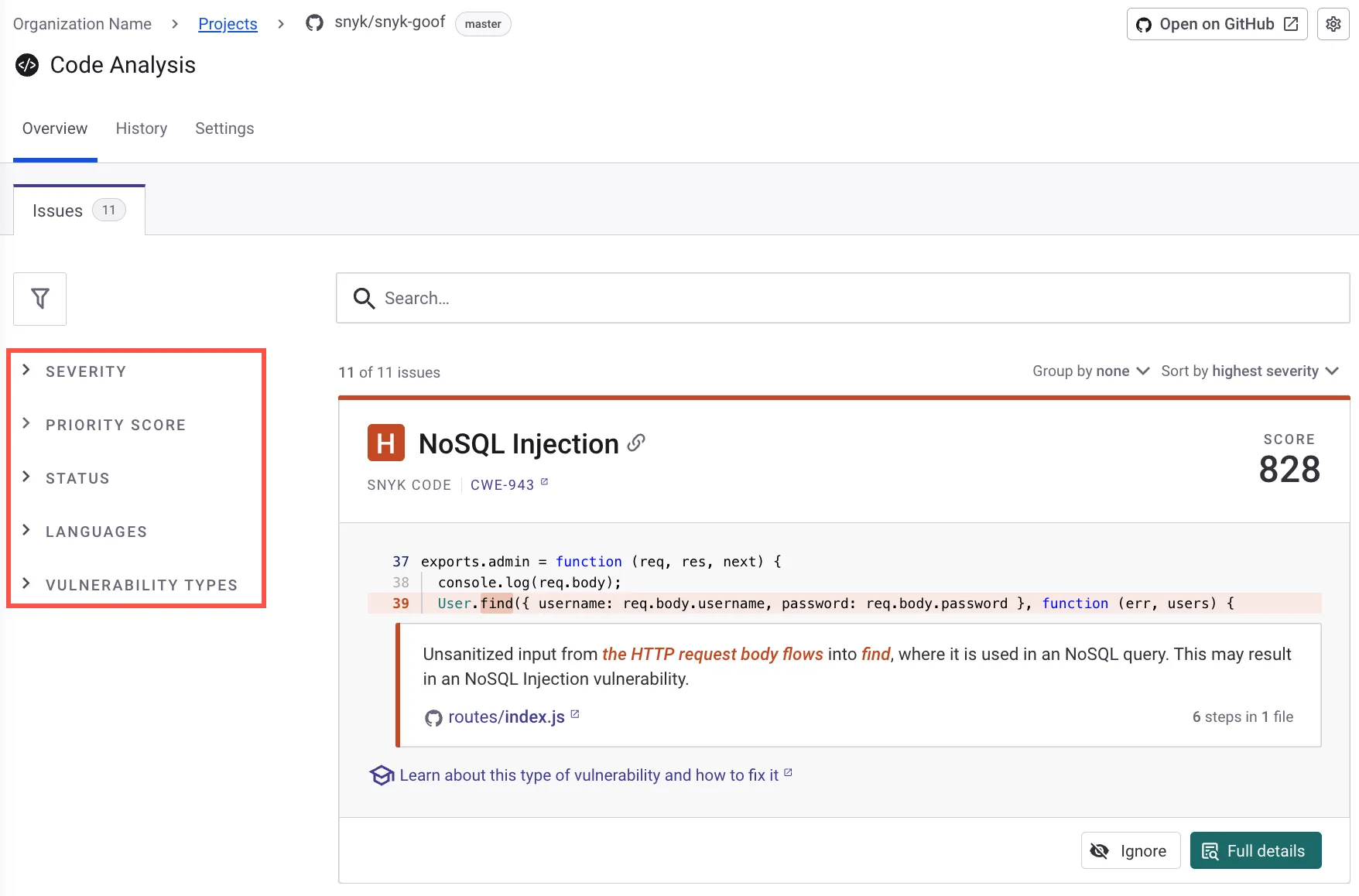
Snyk Open Source identifies vulnerable dependencies by scanning package manifests and lock files. When vulnerabilities are found, it shows the dependency path (direct vs. transitive), severity, exploit maturity, and fix recommendations.
Snyk’s vulnerability database added 24k+ new vulnerabilities in 2024 alone. Risk prioritization evaluates over a dozen factors including reachability, exploit maturity, and EPSS/CVSS scores.
Automated fix pull requests upgrade packages to secure versions. License compliance scanning is available on Team and Enterprise plans.
Snyk Container
Scans Docker and OCI images for vulnerabilities in base OS packages and application dependencies. Analyzes image layers to identify the source of vulnerabilities and recommends secure base image alternatives.
Integrates with Docker Hub, Amazon ECR, Google Artifact Registry, Azure Container Registry, and Harbor.
Snyk IaC
Scans infrastructure as code files for security misconfigurations before cloud deployment. Checks Terraform, CloudFormation, Kubernetes manifests, Helm charts, and Azure ARM templates. Uses CIS benchmarks and threat-modeling research for its rulesets.
Detects issues like S3 buckets without encryption, overly permissive security groups, and pods running as root. Remediation suggestions appear inline with code.
Snyk Studio
Snyk Studio targets AI-generated code. It covers 90% of LLM libraries including OpenAI and Hugging Face.
As AI coding assistants write more production code, this fills the gap between code generation and security validation.
Integrations
Getting started
npm install -g snyk, authenticate with snyk auth, and run snyk test in your build pipeline.When to use Snyk
Snyk works well for teams that want security integrated into developer workflows rather than as a separate scanning stage. The IDE plugins, Git integrations, and automated fix pull requests reduce friction.
Teams running multiple scanning types (SAST, SCA, container, IaC, DAST) benefit from the unified dashboard and policy engine. Managing findings from one platform is simpler than aggregating results from separate tools.
The free tier suits individual developers and small open-source projects. Paid plans scale for teams and enterprises needing unlimited scans, custom rules, SSO, and advanced reporting.
For teams preferring open-source tools, Semgrep CE offers SAST with custom rules and Trivy provides container and IaC scanning. Browse SAST tools and SCA tools to compare options.
For background on how SCA fits into your security program, see What is SCA? and our guide on software supply chain security.