Revenera FlexNet Code Insight is an enterprise SCA platform focused on open-source license compliance, intellectual property protection, and M&A due diligence.
While most SCA tools lead with security, Code Insight places equal weight on license compliance, making it the choice for organizations where licensing carries legal and financial consequences.
The Synopsys 2024 OSSRA report found that 53% of audited codebases contained license conflicts, illustrating why tools like Code Insight exist.
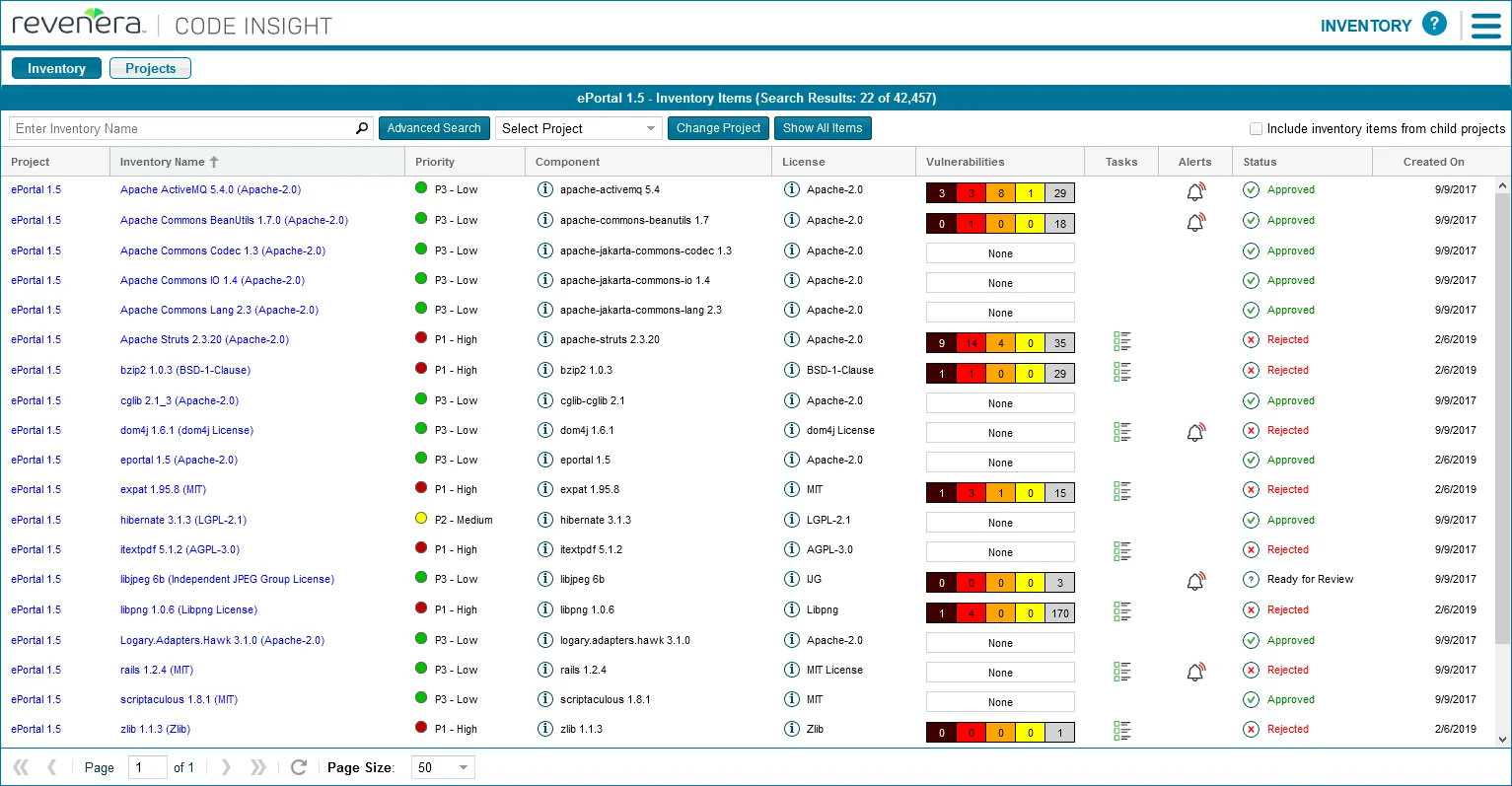
The platform maintains a database of 14M+ open-source components with detailed license information.
It goes beyond identification to provide guidance on license compatibility, attribution requirements, and obligations that may conflict with your business model.
Deep code scanning catches copy-pasted snippets and embedded libraries that dependency-based tools miss.
What is Revenera FlexNet Code Insight?
Code Insight helps software vendors, M&A teams, and regulated enterprises understand what open-source components are in their software, what licenses govern use, and what security vulnerabilities they contain. Workflow features support collaboration between development, legal, and security teams.
Key features
Supported ecosystems
| Ecosystem | Package managers |
|---|---|
| Java/Kotlin | Maven, Gradle, Ant |
| JavaScript | npm, yarn |
| Python | pip, Poetry |
| C/C++ | CMake, Make, Conan |
| Go | Go modules |
| Ruby | Bundler |
| PHP | Composer |
| Rust | Cargo |
| Scala | sbt |
| Source code | Snippet matching against 14M+ components |
| Binaries | JAR, DLL, EXE fingerprinting |
License compliance management
Code Insight provides comprehensive license analysis: detection through multiple methods (declared, embedded text, headers), obligation analysis (attribution, source disclosure, patent grants), compatibility checking, and policy enforcement. It understands nuances that generic scanners miss, such as dual-licensing, license exceptions, and version-specific terms.
Deep code scanning
Unlike dependency-only scanners, Code Insight analyzes source code to find copy-pasted open-source snippets, embedded libraries outside package managers, code matching known projects regardless of modification, and license text scattered throughout codebases.
IP risk assessment
Identifies code from copyleft-licensed projects, detects IP contamination from improperly attributed code, flags patterns matching competitor or contested projects, and provides evidence for M&A due diligence.
Legal workflow integration
Obligation tracking assigns and monitors license obligation completion. Approval workflows route component decisions through designated approvers.
Legal opinions are recorded and linked to specific components. Attribution notices are auto-generated for distribution.
SBOM generation
Generates SBOMs in SPDX, CycloneDX, and custom formats. Includes component inventories, license information, and vulnerability status.
Installation
FlexNet Code Insight is deployed as an enterprise application with several components.
Server Installation
Code Insight runs as a server application that can be deployed on-premises or in cloud environments:
# Download the installer from Revenera support portal
# Run the installation wizard
./CodeInsightInstaller.sh
# Configure database connection
vi /opt/codeinsight/config/database.properties
# Start the server
systemctl start codeinsight
Build Integration
Integrate Code Insight into your build process using plugins and CLI tools:
<!-- Maven plugin configuration -->
<plugin>
<groupId>com.revenera</groupId>
<artifactId>codeinsight-maven-plugin</artifactId>
<version>2024.1</version>
<configuration>
<serverUrl>https://codeinsight.example.com</serverUrl>
<apiKey>${CODEINSIGHT_API_KEY}</apiKey>
<projectName>${project.name}</projectName>
<failOnPolicyViolation>true</failOnPolicyViolation>
</configuration>
<executions>
<execution>
<goals>
<goal>scan</goal>
</goals>
</execution>
</executions>
</plugin>
// Gradle plugin
plugins {
id 'com.revenera.codeinsight' version '2024.1'
}
codeInsight {
serverUrl = 'https://codeinsight.example.com'
apiKey = System.getenv('CODEINSIGHT_API_KEY')
projectName = project.name
failOnPolicyViolation = true
}
CLI Scanner
For languages without build plugins, use the command-line scanner:
# Scan a directory
codeinsight-cli scan \
--server https://codeinsight.example.com \
--api-key $CODEINSIGHT_API_KEY \
--project "MyProject" \
--path /path/to/source
# Scan with specific policies
codeinsight-cli scan \
--server https://codeinsight.example.com \
--api-key $CODEINSIGHT_API_KEY \
--project "MyProject" \
--path /path/to/source \
--policy "Copyleft-Prohibited"
Integration
CI/CD Pipeline Integration
# GitHub Actions example
name: License Compliance Check
on:
pull_request:
branches: [main]
jobs:
license-scan:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
with:
fetch-depth: 0 # Full history for better detection
- name: Download Code Insight CLI
run: |
curl -L "$CODEINSIGHT_CLI_URL" -o codeinsight-cli.tar.gz
tar -xzf codeinsight-cli.tar.gz
- name: Run compliance scan
env:
CODEINSIGHT_API_KEY: ${{ secrets.CODEINSIGHT_API_KEY }}
CODEINSIGHT_URL: ${{ secrets.CODEINSIGHT_URL }}
run: |
./codeinsight-cli scan \
--server $CODEINSIGHT_URL \
--api-key $CODEINSIGHT_API_KEY \
--project "${{ github.repository }}" \
--path . \
--output scan-results.json
- name: Check for policy violations
run: |
VIOLATIONS=$(jq '.policyViolations | length' scan-results.json)
if [ "$VIOLATIONS" -gt 0 ]; then
echo "Found $VIOLATIONS policy violations"
jq '.policyViolations[] | "\(.component): \(.policy)"' scan-results.json
exit 1
fi
- name: Upload SBOM artifact
uses: actions/upload-artifact@v4
with:
name: sbom
path: scan-results.json
# GitLab CI example
stages:
- compliance
license-scan:
stage: compliance
image: openjdk:17-slim # Download CLI from Revenera portal
script:
- |
codeinsight-cli scan \
--server $CODEINSIGHT_URL \
--api-key $CODEINSIGHT_API_KEY \
--project "$CI_PROJECT_NAME" \
--path . \
--fail-on-policy-violation
artifacts:
reports:
spdx: codeinsight-sbom.spdx
rules:
- if: $CI_PIPELINE_SOURCE == "merge_request_event"
IDE Integration
Code Insight provides IDE plugins for early detection:
- VS Code Extension: Real-time license feedback as you add dependencies
- IntelliJ Plugin: License information in dependency views
- Eclipse Plugin: Integration with Java development workflow
Legal System Integration
Export compliance data to legal and procurement systems:
# Generate attribution report
codeinsight-cli report \
--server $CODEINSIGHT_URL \
--api-key $CODEINSIGHT_API_KEY \
--project "MyProject" \
--type attribution \
--output attribution-notice.txt
# Export to legal workflow system
codeinsight-cli export \
--server $CODEINSIGHT_URL \
--api-key $CODEINSIGHT_API_KEY \
--project "MyProject" \
--format csv \
--output components-for-legal.csv
Setup
When to use Revenera FlexNet Code Insight
Code Insight fits organizations where license compliance carries legal and financial consequences: software vendors, M&A scenarios, and regulated industries.
Strengths:
- 14M+ component database with detailed license data
- Deep code scanning for snippets and embedded libraries
- IP risk assessment for M&A due diligence
- Legal team collaboration workflows
- Attribution notice generation
Limitations:
- Heavier setup than developer-first tools
- Commercial only, no free tier
- Security features less developed than dedicated security-first SCA tools
- Primarily on-premises deployment
How it compares:
| vs. | Key difference |
|---|---|
| Black Duck | Both strong on license compliance. Black Duck has a larger knowledge base and binary scanning. Code Insight has deeper legal workflow integration and IP risk assessment. |
| FOSSA | FOSSA has a more modern UX and developer-friendly approach. Code Insight has deeper legal workflow features and M&A due diligence capabilities. |
| SCANOSS | SCANOSS also detects code snippets but is lighter-weight and open-source. Code Insight adds legal workflows, obligation tracking, and attribution generation. |
Further reading: Open Source License Compliance | What is SCA? | What is SBOM?