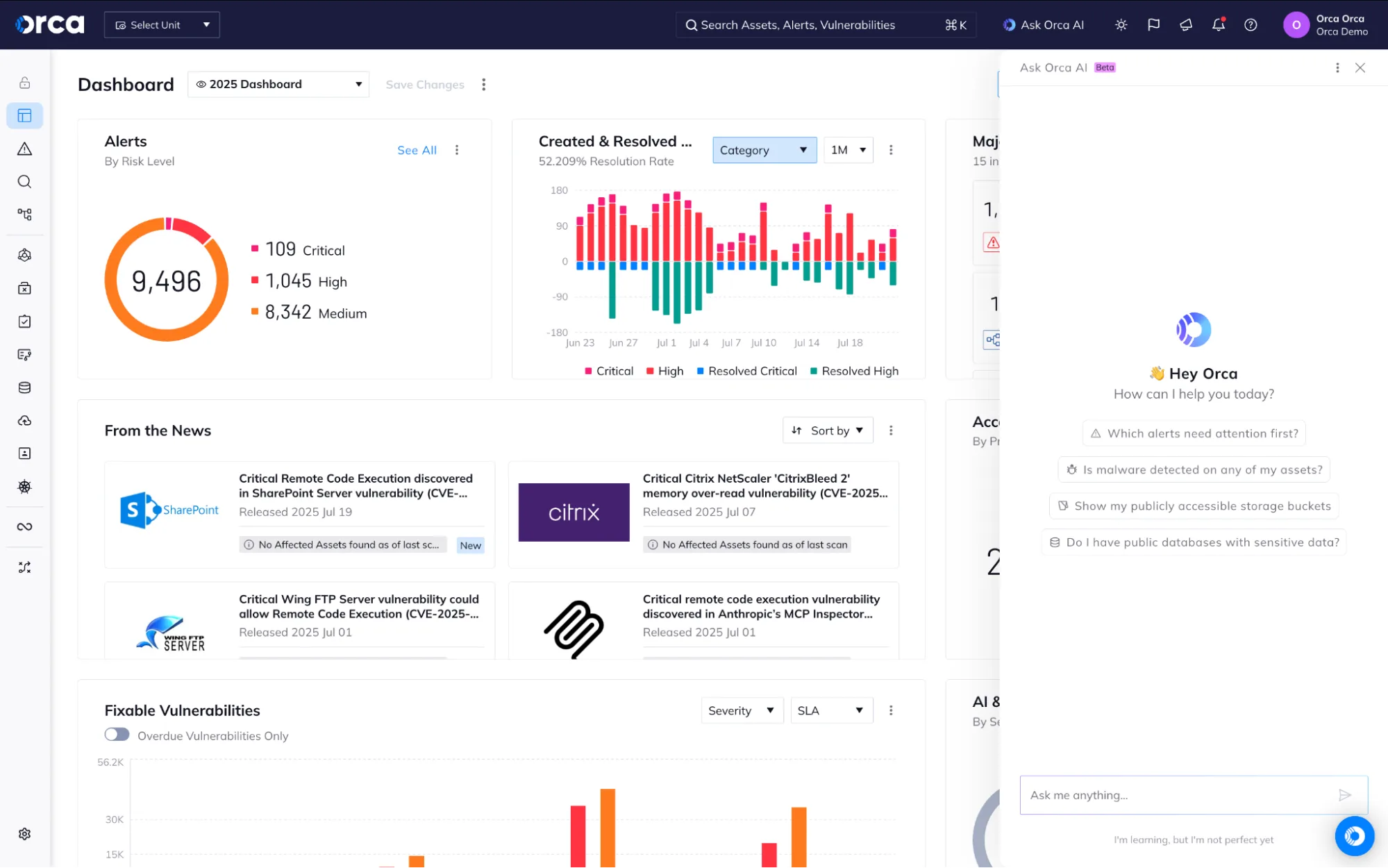
Orca Security is an agentless Cloud Native Application Protection Platform built on patented SideScanning technology. The platform provides workload-deep visibility across cloud environments, avoiding the agent deployment overhead associated with traditional solutions.
Founded in 2019 with 350 employees across London, Tel Aviv, and Portland, Orca serves enterprise customers including Autodesk, Unity, SAP, Sisense, and Lemonade. The platform is FedRAMP Moderate Authorized, SOC 2 Type II certified, and holds ISO 27001/27017/27018/27701 certifications.
What is Orca Security?
Orca Security delivers comprehensive cloud infrastructure security and compliance through a single agentless platform. The solution combines Cloud Security Posture Management (CSPM), Cloud Workload Protection Platform (CWPP), Cloud Infrastructure Entitlement Management (CIEM), and Data Security Posture Management (DSPM).
The platform’s SideScanning technology reads cloud workload data without deploying agents or running code in customer environments. This approach provides visibility into virtual machines, containers, serverless functions, and cloud infrastructure resources including storage buckets, VPCs, and KMS keys.
Orca automatically includes new assets when they’re added to cloud environments, eliminating manual configuration and ensuring continuous coverage. The platform centralizes all cloud security findings in a single interface, allowing security teams to query, investigate, and understand risks with full context.
Key Features
| Module | Details |
|---|---|
| CSPM | Cloud Security Posture Management across AWS, Azure, GCP |
| CWPP | Cloud Workload Protection for VMs, containers, serverless |
| CIEM | Cloud Infrastructure Entitlement Management |
| DSPM | Data Security Posture Management for PII/PHI detection |
| CDR | Cloud Detection and Response with 24x7 monitoring |
| API Security | API discovery, posture management, drift detection |
| AI-SPM | AI Security Posture Management for cloud AI models |
| Compliance | 100+ frameworks including PCI-DSS, HIPAA, SOC 2, ISO 27001, CIS |
| Runtime | Orca Sensor with eBPF-based visibility and prevention |
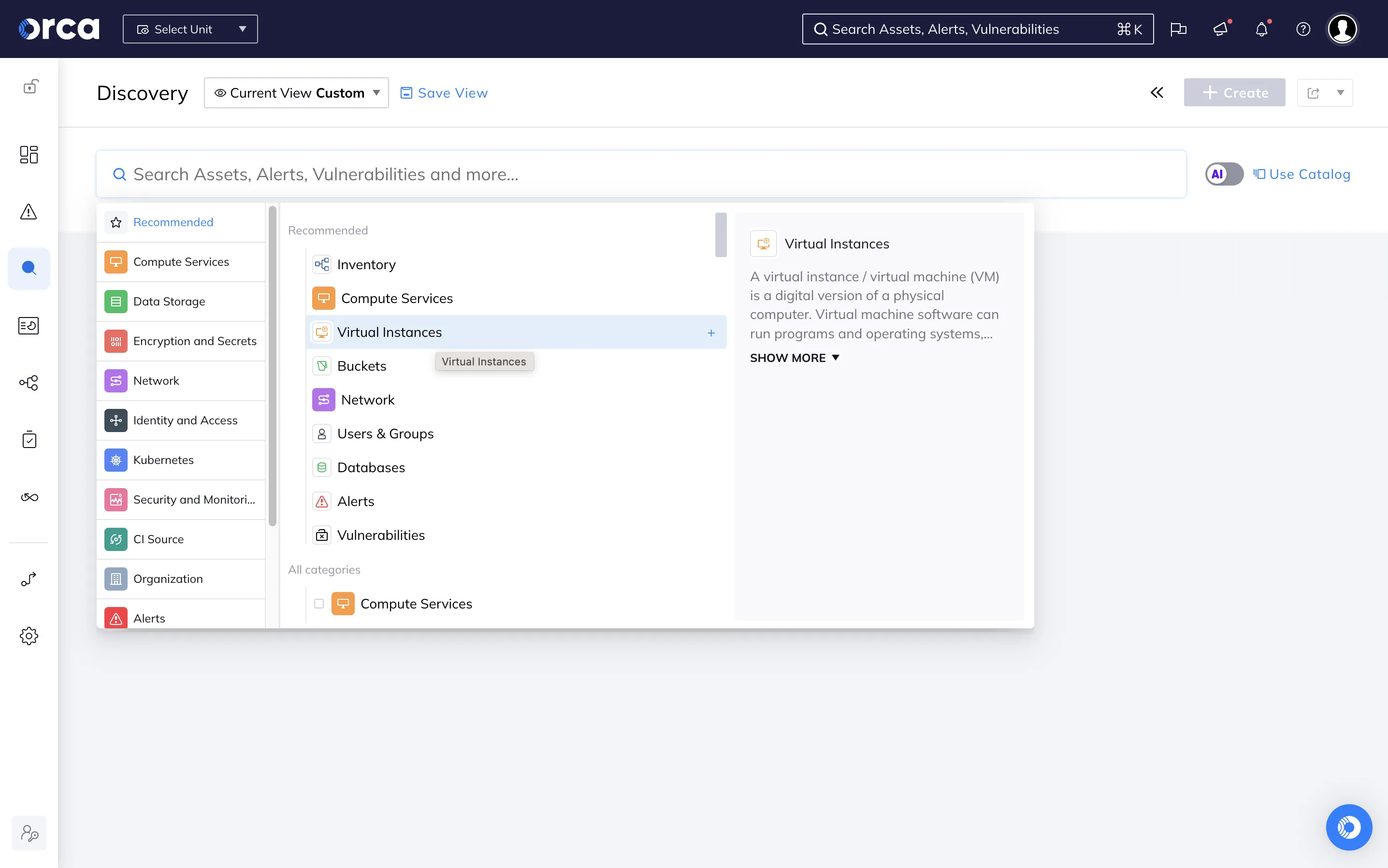
SideScanning Technology
Orca’s patented SideScanning technology provides the foundation for agentless cloud security. The platform connects to cloud provider APIs and reads workload runtime data, configurations, and file systems without sending packets over customer networks or executing code in production environments.
This approach eliminates deployment friction associated with agent-based tools. Organizations avoid dealing with agent installation, compatibility issues, performance impacts, and operational overhead.
SideScanning provides consistent coverage across all workload types including legacy systems, ephemeral containers, and serverless functions.
Orca reads running processes, installed packages, file permissions, and network connections without modifying customer environments. The Orca Sensor adds eBPF-based runtime visibility for organizations that want real-time prevention alongside agentless scanning.
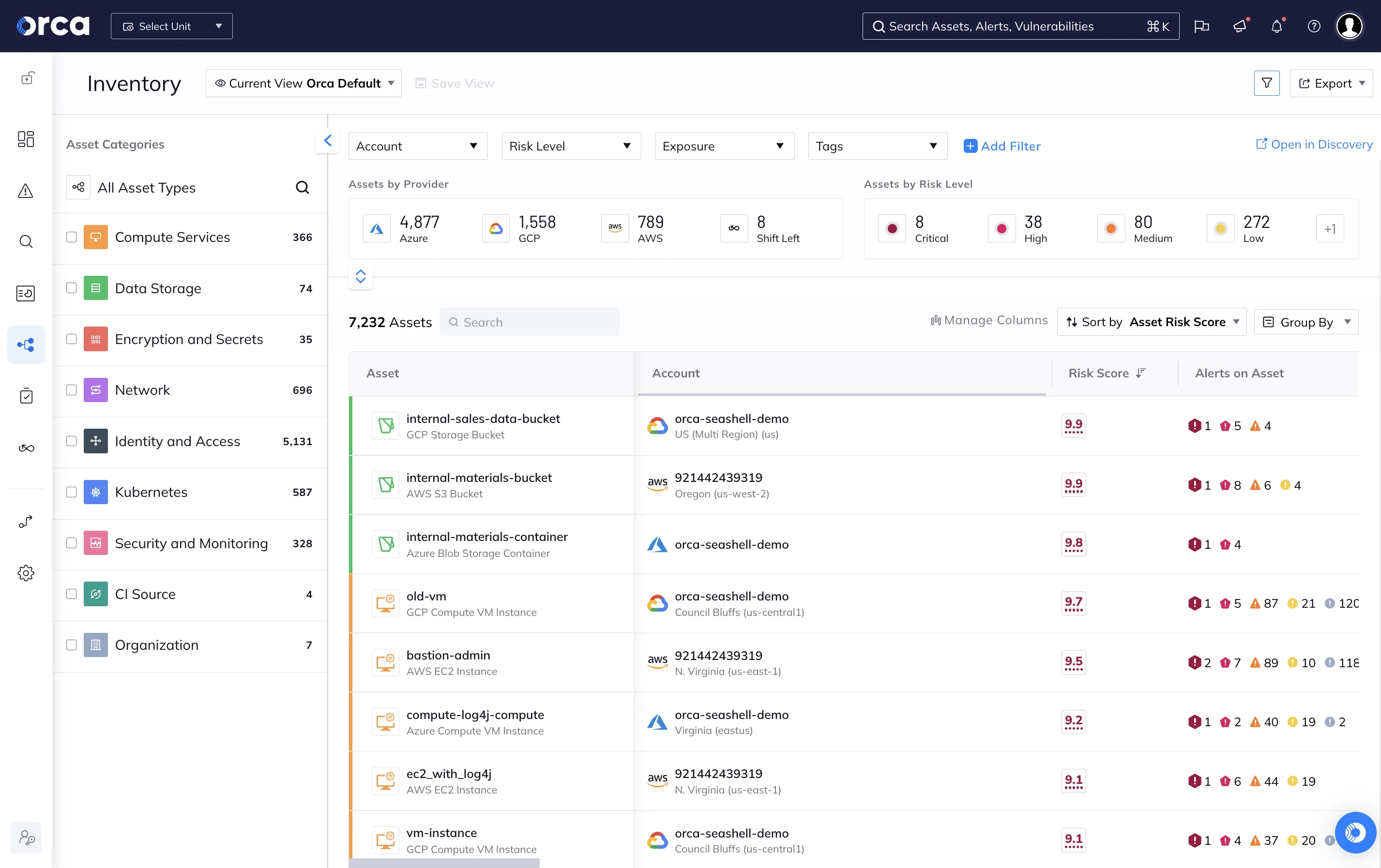
Comprehensive Asset Coverage
Orca automatically discovers and secures all cloud assets including compute instances, containers, Kubernetes clusters, serverless functions, databases, storage buckets, identity systems, and networking components. The platform maintains real-time inventory of cloud resources across AWS, Azure, and GCP.
New assets are automatically included in security scans without manual configuration. This coverage eliminates visibility gaps in dynamic cloud environments.
Cloud Security Posture Management
CSPM capabilities identify misconfigurations across cloud infrastructure that create security risks or compliance violations. Orca scans cloud services, networking settings, identity configurations, and data stores against security best practices and compliance frameworks.
The platform detects exposed storage buckets, overly permissive security groups, unencrypted data, excessive IAM permissions, and configuration drift from security baselines. Automated remediation guidance accelerates fixing misconfigurations before they’re exploited.
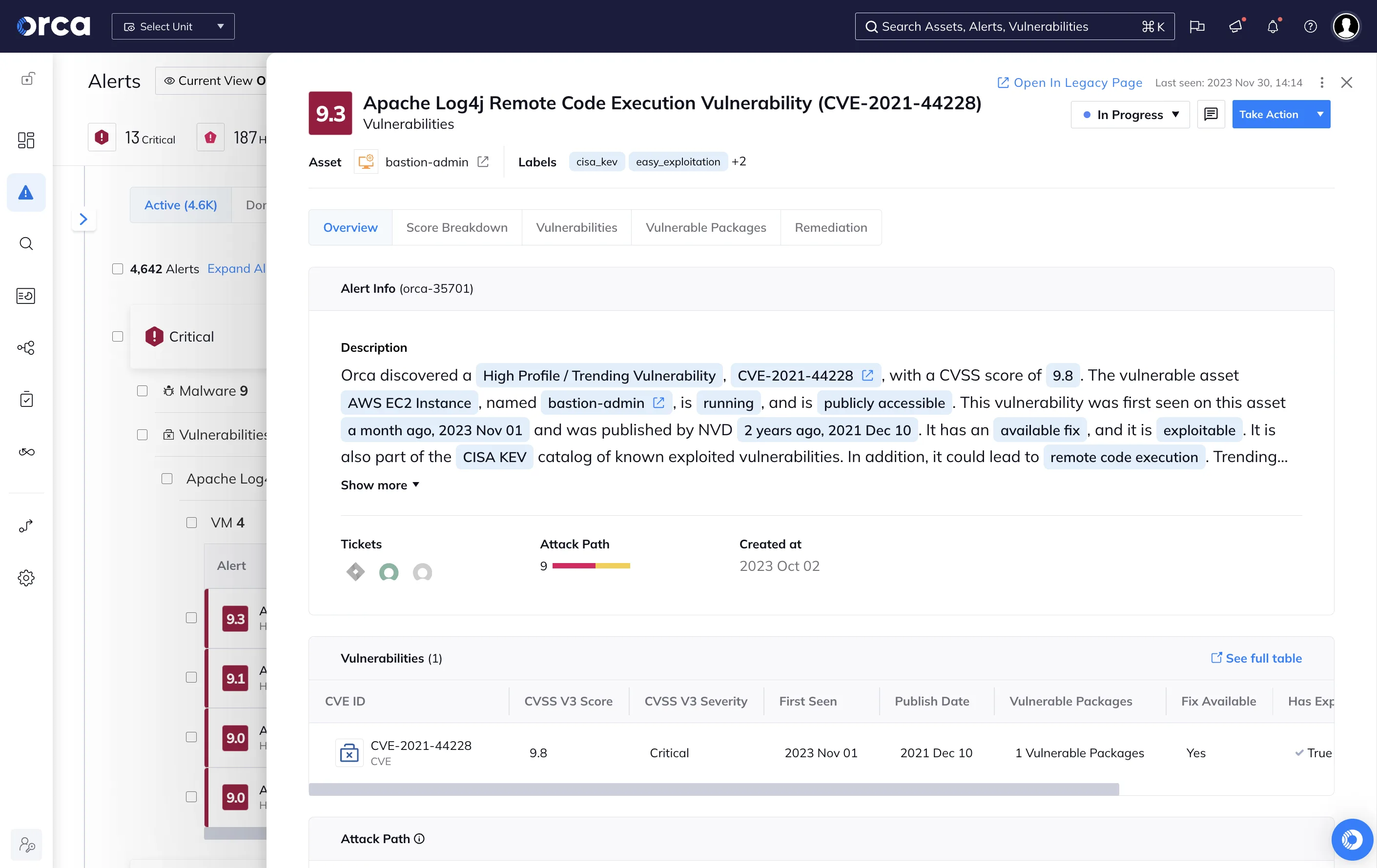
Vulnerability Management
Orca provides comprehensive vulnerability scanning for operating systems, packages, libraries, and application dependencies across all cloud workloads. The platform identifies CVEs and assigns risk scores based on severity, exploitability, and asset criticality.
Unlike traditional vulnerability scanners, Orca correlates vulnerability data with network exposure, running processes, and access privileges. This context enables prioritization of vulnerabilities that are actually reachable and pose real risk to production environments.
AI-Driven Risk Prioritization
Orca AI (the platform’s GenAI assistant) analyzes security findings and identifies which issues require immediate attention. Risk prioritization considers vulnerability severity, asset criticality, network exposure, exploit availability, and business context.
Data Security Posture Management
DSPM features discover sensitive data across cloud storage, databases, and compute resources. The platform classifies data based on content and context, identifying PII, PHI, financial information, and intellectual property.
Orca monitors data access patterns, encryption status, and exposure risks. The platform alerts on publicly accessible sensitive data, unencrypted databases, and excessive data access permissions. This visibility helps organizations maintain data security and compliance.
API Security Monitoring
The platform discovers and inventories APIs across cloud environments, tracking API endpoints, authentication methods, and data flows. Orca identifies shadow APIs, deprecated endpoints, and APIs with security vulnerabilities.
API security monitoring includes authentication testing, authorization validation, and detection of common API vulnerabilities like injection flaws and broken object-level authorization. Integration with application security provides end-to-end API protection.
Compliance Automation
Orca includes pre-built compliance frameworks for PCI-DSS, HIPAA, SOC 2, ISO 27001, GDPR, NIST, and CIS benchmarks. The platform continuously monitors cloud configurations against compliance requirements and generates audit-ready reports.
Compliance dashboards show policy violations, remediation status, and historical trends. Automated evidence collection reduces manual compliance work and simplifies audit preparation. Custom policy frameworks support organization-specific requirements.
Getting Started
When to Use Orca Security
Orca Security is designed for organizations seeking comprehensive cloud security without the operational overhead of agent-based solutions. The platform excels in dynamic cloud environments where workloads scale rapidly and asset inventory changes frequently.
Strengths
The agentless SideScanning technology provides complete cloud visibility without deployment complexity, performance impacts, or agent management overhead. Organizations achieve full cloud risk assessment within 24 hours of deployment, significantly faster than agent-based alternatives.
Orca’s unified CNAPP platform eliminates the need for multiple point solutions. Security teams manage CSPM, CWPP, CIEM, DSPM, vulnerability management, and compliance from a single interface. This consolidation reduces tool sprawl and improves operational efficiency.
AI-driven risk prioritization helps teams focus on issues that matter. The platform filters thousands of security findings to highlight vulnerabilities and misconfigurations that pose real risk to production environments. This approach reduces alert fatigue and accelerates remediation.
Limitations
Orca is purpose-built for cloud environments and does not cover on-premises infrastructure. Organizations with hybrid deployments may need complementary solutions for data center security.
The platform requires cloud provider API access for SideScanning. Organizations with strict API access controls or air-gapped cloud environments may face deployment challenges.
Pricing is based on cloud workload count and may not align with all budget structures.
For a broader view of CNAPP platforms, see our cloud infrastructure security guide. Orca focuses on infrastructure and platform security rather than application code analysis.
Development teams seeking SAST tools or code-level vulnerability detection should consider complementary application security solutions.