Objection is a runtime mobile security exploration toolkit developed by SensePost that simplifies mobile application security testing.
With over 8,900 GitHub stars, it has become a popular choice for pentesters who need quick assessment capabilities without the complexity of writing Frida scripts from scratch.
Released in January 2026, Objection is actively maintained as an instrumented mobile pentest framework.
The tool’s primary advantage is accessibility. While Frida requires JavaScript knowledge and custom hook development, Objection provides a command-line interface with pre-built commands for common security testing tasks.
This makes it ideal for rapid assessments and for testers who want powerful capabilities without deep instrumentation expertise.
What is Objection?
Objection is a Python-based toolkit that leverages Frida’s dynamic instrumentation capabilities to perform runtime analysis of iOS and Android applications. It injects scripts into running processes to bypass security controls, inspect application internals, and manipulate behavior—all without modifying the original APK or IPA permanently.
The framework operates as a command-line REPL (Read-Eval-Print Loop) where you can execute commands against a running mobile app. This interactive approach lets you explore the app dynamically, responding to what you discover rather than planning all tests in advance.
Installation is straightforward via pip (pip3 install objection), and the tool handles the complexity of Frida setup behind the scenes. For apps on non-jailbroken or non-rooted devices, Objection can patch APKs and IPAs to embed frida-gadget, enabling testing without system-level access.
Key features
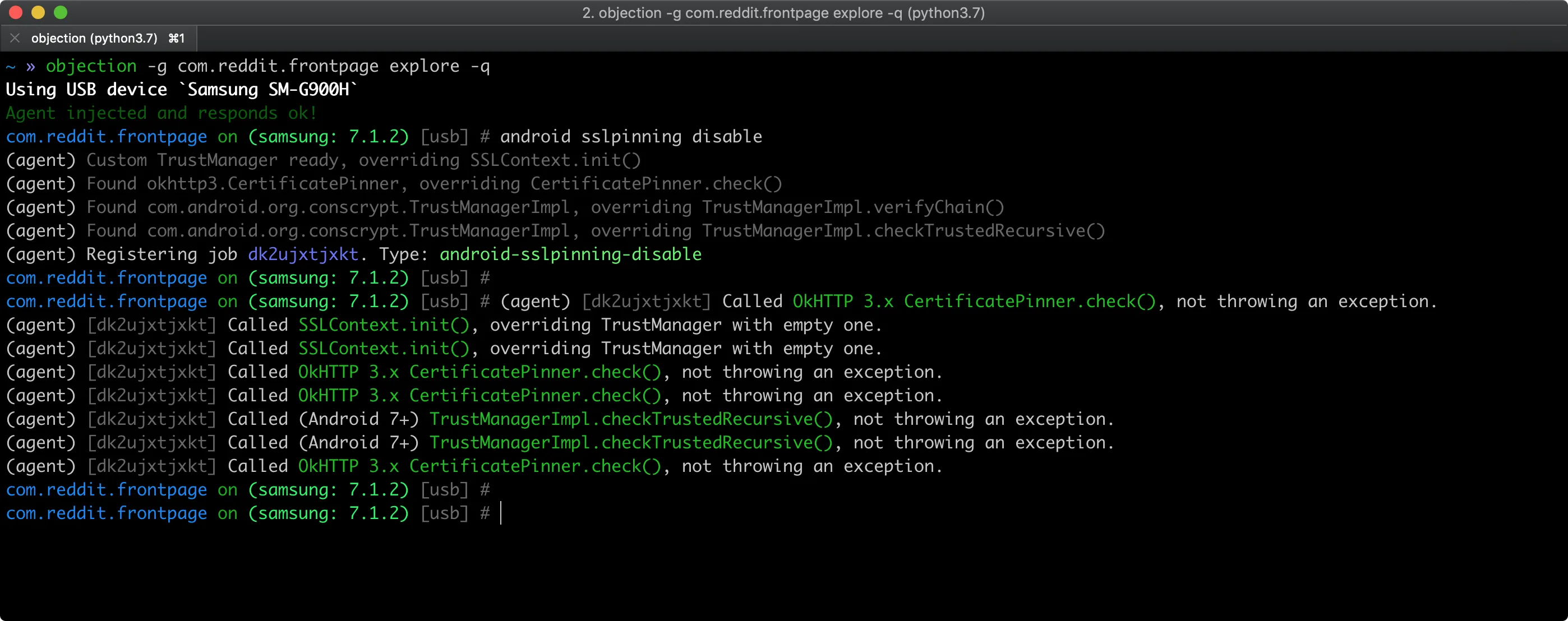
SSL Pinning Bypass
One of Objection’s most popular features is automated SSL certificate pinning bypass.
With a single command (ios sslpinning disable or android sslpinning disable), you can defeat most pinning implementations, allowing you to intercept HTTPS traffic with mitmproxy or Burp Suite.
This eliminates hours of manual hook writing for a task that’s essential to most mobile pentests.
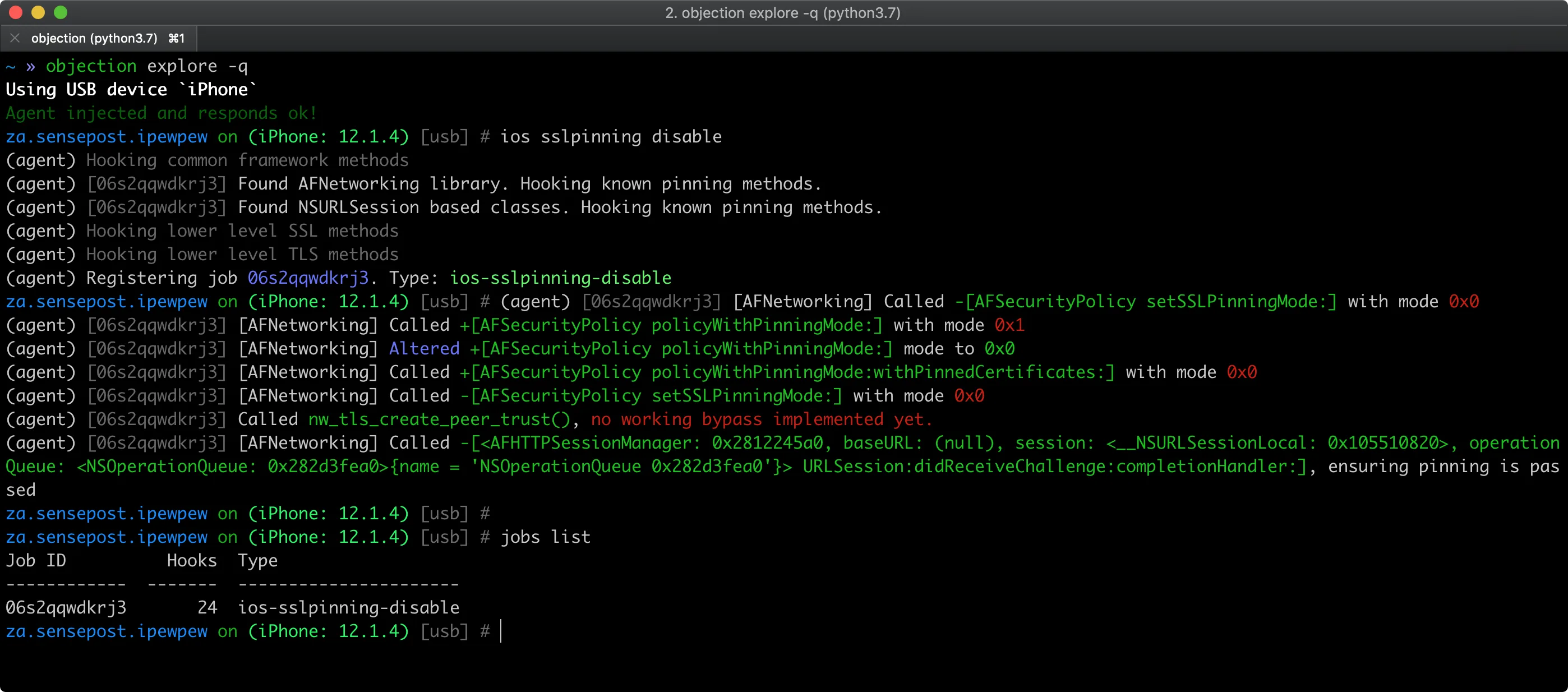
The SSL pinning bypass works by hooking common pinning libraries and custom implementations at runtime. It covers frameworks like AFNetworking on iOS and OkHttp on Android, as well as many custom validation routines.
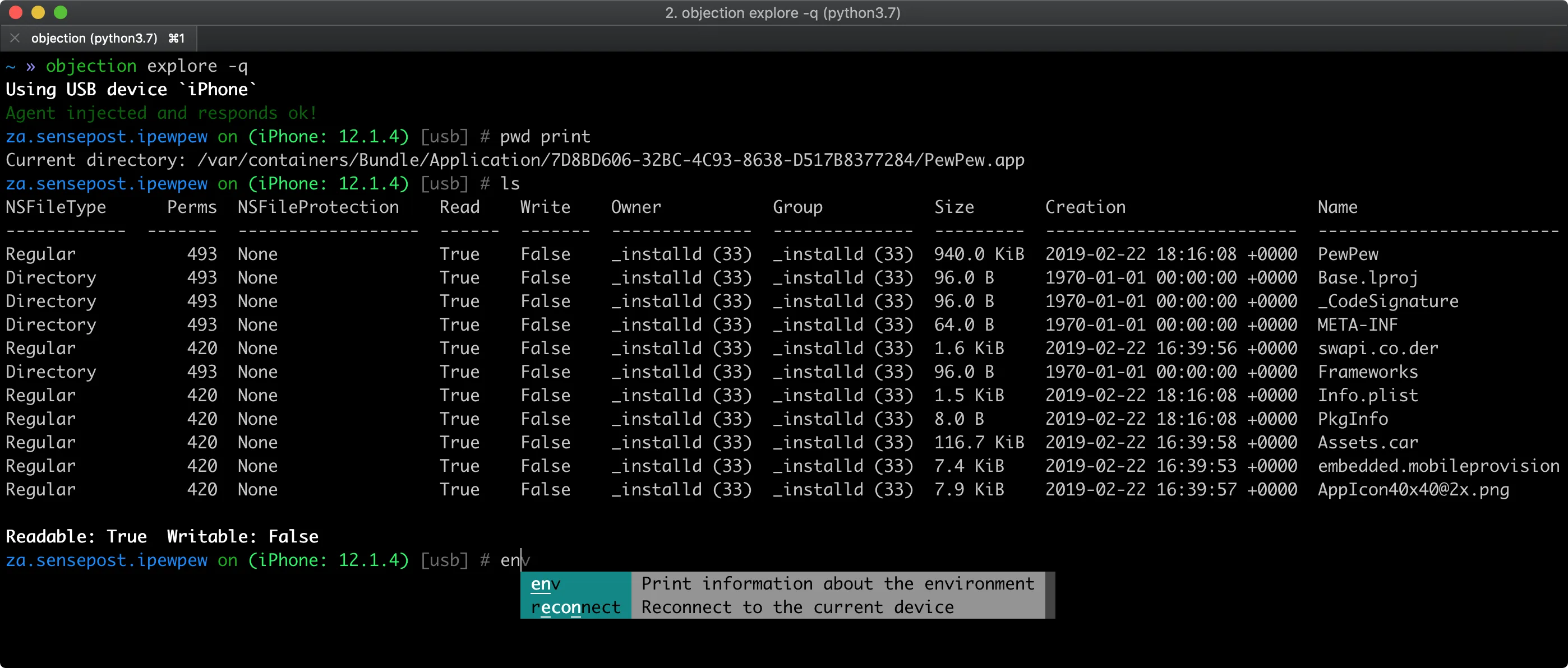
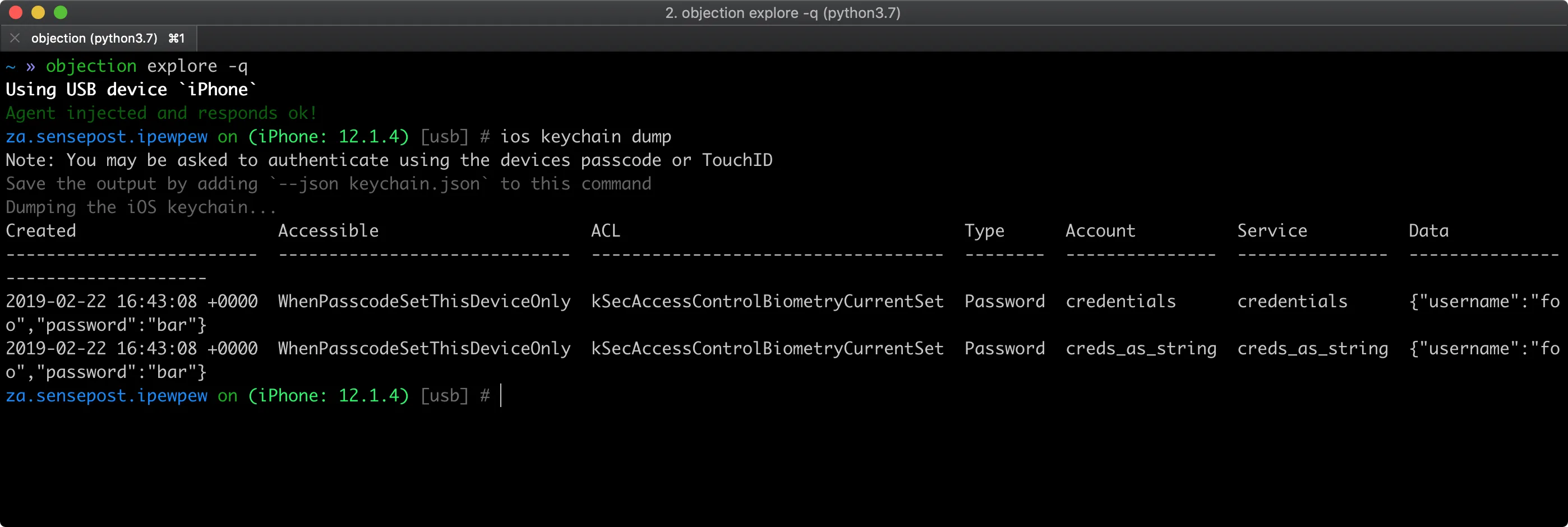
File System and Container Exploration
Objection provides commands to browse the app’s file system, download databases and configuration files, and upload modified versions for testing.
On iOS, you can navigate the app’s Documents, Library, and tmp directories. On Android, you can explore /data/data/
This capability is invaluable for finding hardcoded credentials, examining SQLite databases for sensitive data, and understanding how the app stores information locally. You can dump binary cookies, inspect plist files, and analyze local encryption implementations.
Memory and Heap Analysis
The toolkit includes commands for memory dumping and heap exploration. You can search process memory for sensitive strings like API keys or tokens, dump objects from the heap to understand runtime state, and identify where sensitive data resides in RAM.
These features help identify insecure data storage vulnerabilities where apps keep sensitive information in memory longer than necessary or fail to zero out credentials after use.
Integration with Mobile Security Workflows
Objection fits naturally into comprehensive mobile testing workflows. Start by decompiling the APK with Jadx to understand the app’s structure and identify interesting classes or methods.
Then use Objection to hook those methods at runtime, modify their behavior, and observe the results.
For apps with native libraries, combine Objection with Ghidra for reverse engineering the compiled code, then use Objection’s custom hook capabilities to test your findings. The framework also integrates with Frida scripts, allowing you to extend Objection with custom functionality when needed.
App Patching for Non-Rooted Testing
The objection patchapk (Android) and objection patchipa (iOS) commands automate the process of embedding frida-gadget into apps. This allows you to test on non-rooted Android devices and non-jailbroken iOS devices, significantly expanding the range of devices you can use for testing.
The patched app behaves identically to the original but includes the Frida runtime, enabling full Objection capabilities without system-level privileges.
When to use Objection
Strengths:
- Significantly faster assessment than writing custom Frida scripts
- Beginner-friendly interface with extensive documentation
- Covers the most common mobile pentest tasks out of the box
- Active development with regular updates and new features
- Strong community and cheat sheets available online
- Works without jailbreak/root via app patching
- Free and open source under GPL-3.0
- Cross-platform support for iOS and Android
Limitations:
- Less flexible than custom Frida scripting for complex scenarios
- Pre-built hooks may not work on heavily customized implementations
- Requires some learning of command syntax and options
- App patching may trigger anti-tampering detections
- Performance overhead from multiple simultaneous hooks
- Some advanced techniques still require dropping to raw Frida
Getting started
pip3 install objection to install the toolkit and its dependencies including Frida.objection -g com.example.app explore to launch the interactive REPL.objection patchapk -s app.apk, install the patched app, run it, then connect with objection explore.ios sslpinning disable to bypass pinning, android hooking list activities to enumerate components, or env to inspect the app’s file system paths.Combine Objection with mitmproxy for traffic interception, Jadx for static analysis, and Frida scripts when you need custom capabilities beyond Objection’s built-in commands.