ModSecurity is an open-source web application firewall engine that provides real-time protection for web applications running on Apache, IIS, and Nginx. The platform uses an event-based programming language to monitor HTTP traffic, detect attacks, and enforce security policies.
Started in 2002, ModSecurity became one of the most widely deployed open-source WAF engines. The project transferred from Trustwave to OWASP in January 2024. Trustwave sponsored development through July 2024, and the project now has 9,500 GitHub stars and an active contributor community.
What is ModSecurity?
ModSecurity is a cross-platform web application firewall engine designed to protect applications from a range of attacks including SQL injection, cross-site scripting, and other OWASP Top 10 vulnerabilities. The platform operates as an embedded security component within web servers, analyzing HTTP requests and responses in real-time.
The WAF engine uses a flexible rule language that allows security teams to define custom protection logic matching their application requirements. ModSecurity rules can inspect request headers, cookies, query parameters, POST data, uploaded files, and response bodies to identify malicious patterns.
ModSecurity version 3.0 (libmodsecurity) introduced a modular architecture that separates the WAF engine into a standalone library. This design communicates with web servers through connectors for Apache, Nginx, and IIS, enabling easier integration and maintenance compared to earlier tightly-coupled implementations.
Key features
| Feature | Details |
|---|---|
| Web servers | Apache HTTP Server, Nginx, Microsoft IIS |
| Architecture | libmodsecurity (v3) with platform connectors |
| Language | C++17 with Flex/Yacc parser |
| Rule set | OWASP Core Rule Set (CRS) with paranoia levels |
| Dependencies | YAJL (JSON), libpcre (regex), libXML2 (XML parsing) |
| Optional deps | libinjection (@detectXSS, @detectSQL), curl (SecRemoteRules) |
| Bindings | Python, Rust, Varnish (community-maintained) |
| License | Apache License 2.0 |
Cross-platform support
ModSecurity runs on Apache HTTP Server, Microsoft IIS, and Nginx through dedicated modules and connectors. The libmodsecurity architecture enables consistent security functionality across different web server platforms.
Apache integration uses mod_security2 module for versions 2.x and mod_security3 for version 3.x. Nginx integration uses the ModSecurity-nginx connector. IIS support provides Windows-based deployments with equivalent protection capabilities.
Cross-platform consistency means security rules written for one web server work on others with minimal modifications. This portability simplifies security policy management in heterogeneous infrastructure environments.
Event-Based Rule Language
ModSecurity’s rule language provides powerful capabilities for defining security logic based on HTTP transaction events. Rules can execute actions during request processing phases including URI, request headers, request body, response headers, and response body phases.
The rule engine supports variables, operators, transformations, and actions that enable complex security policies. Variables access request and response data, operators perform matching logic, transformations normalize data before matching, and actions define responses to rule matches.
Chained rules allow building sophisticated detection logic by combining multiple conditions. Persistent storage capabilities enable tracking state across multiple requests to identify attack patterns that span multiple transactions.
OWASP Core Rule Set
ModSecurity integrates seamlessly with OWASP Core Rule Set (CRS), a collection of generic attack detection rules. CRS provides immediate protection against SQL injection, cross-site scripting, remote file inclusion, and other common web application attacks.
The rule set uses paranoia levels to balance security and false positives. Lower paranoia levels provide broader compatibility with diverse applications while higher levels enable stricter security with potential for false positives requiring tuning.
CRS receives regular updates as new attack techniques emerge. The community-driven development model ensures the rule set evolves to address current threat landscapes.
Request and Response Filtering
ModSecurity inspects both HTTP requests and responses to detect attacks and data leakage. Request filtering analyzes incoming traffic for malicious payloads while response filtering prevents sensitive data exposure.
Request inspection covers HTTP methods, URIs, query strings, headers, cookies, and body content. The engine can parse multipart data, JSON, and XML to inspect structured content within requests.
Response filtering identifies sensitive information like credit card numbers, social security numbers, and error messages that shouldn’t be exposed to clients. This capability helps prevent data leakage and information disclosure vulnerabilities.
Real-Time Monitoring
The platform monitors HTTP traffic in real-time, analyzing transactions as they occur. Real-time analysis enables immediate blocking of malicious requests before they reach application code.
Monitoring operates inline within the web server request processing pipeline. This positioning allows ModSecurity to make request handling decisions including allowing, blocking, redirecting, or logging transactions based on rule evaluations.
Real-time capabilities extend to dynamic rule updates. Security teams can modify rules without restarting web servers, enabling rapid response to emerging threats or false positive issues.
Audit Logging
ModSecurity provides comprehensive audit logging that records transaction details when rules trigger. Audit logs capture request and response data, matched rules, and processing actions for security investigation and compliance.
Log formats include detailed text-based logs and structured JSON output compatible with log analysis tools. Logging can be configured to capture all transactions, only blocked requests, or custom criteria matching security monitoring requirements.
Audit logs support forensic analysis of attacks, troubleshooting false positives, and compliance reporting. The platform integrates with SIEM systems and log aggregators for centralized security monitoring.
Geolocation and IP Reputation
ModSecurity supports integration with geolocation databases and IP reputation services to enhance attack detection. Geolocation capabilities enable blocking requests from specific countries or regions.
IP reputation integration allows rules to consider source IP trustworthiness when making security decisions. Known malicious IPs can be blocked while trusted IPs receive less restrictive inspection.
These contextual capabilities help reduce false positives by adjusting security policies based on request origin characteristics. Organizations can implement defense-in-depth strategies that combine multiple risk signals.
ModSecurity 3.x Architecture
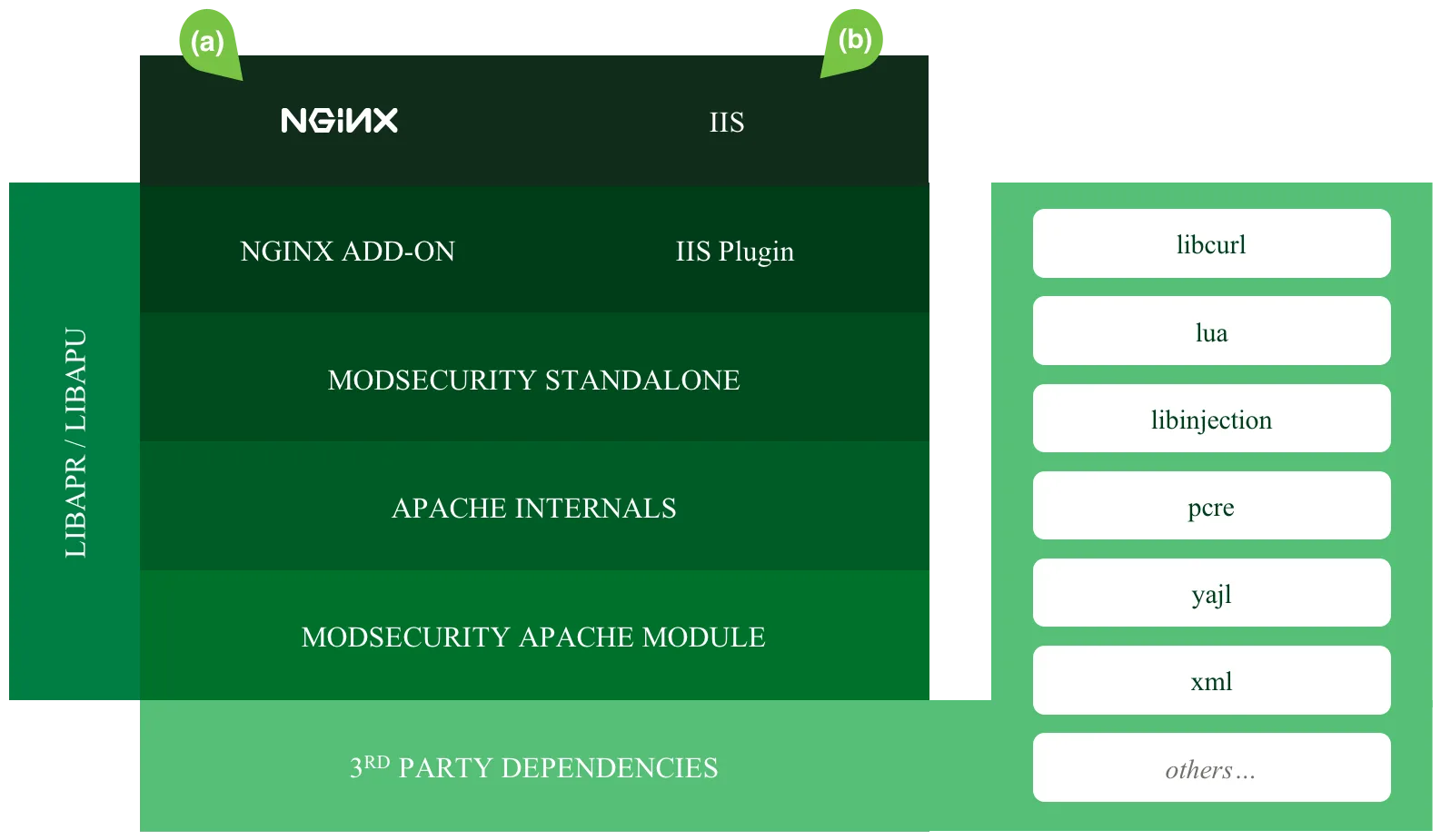
The libmodsecurity architecture in version 3.x separates the WAF engine from web server integration code. This modular design improves maintainability and enables easier porting to new platforms.
Web server connectors use a standard API to communicate with the libmodsecurity engine. This separation means engine improvements benefit all supported platforms without requiring connector modifications.
The architecture supports advanced deployment scenarios including running ModSecurity as a reverse proxy, API gateway integration, and Kubernetes ingress controller protection.
ModSecurity Rules and Configuration
Effective ModSecurity deployment requires rule configuration matching application requirements. Organizations can use OWASP CRS as a baseline and add custom rules for application-specific protection.
Rule tuning involves adjusting CRS paranoia levels, whitelisting legitimate requests that trigger rules, and disabling rules incompatible with specific applications. The tuning process balances security coverage with operational compatibility.
Custom rules extend protection for organization-specific threats including business logic attacks, API abuse, and application-specific vulnerabilities. The rule language provides flexibility to implement precisely targeted protection logic.
Getting started
./build.sh && ./configure && make && sudo make install. Requires YAJL, libpcre, and libXML2 as dependencies.When to use ModSecurity
ModSecurity is ideal for organizations seeking open-source web application protection without licensing costs. The platform works well for teams with security expertise who can configure and tune rules effectively.
Strengths
As one of the most widely deployed open-source WAF engines, ModSecurity benefits from extensive community support and maturity. The Apache License 2.0 enables free use, modification, and distribution without restrictions.
OWASP Core Rule Set provides immediate protection against common attacks with minimal configuration. Organizations gain security value quickly while retaining flexibility to customize protection based on specific requirements.
Cross-platform support enables consistent security across Apache, IIS, and Nginx deployments. The modular architecture in version 3.x simplifies integration and supports diverse deployment scenarios including containers and Kubernetes.
The flexible rule language supports advanced security logic beyond basic pattern matching. Security teams can implement custom protection for business logic vulnerabilities, API security, and application-specific attacks.
Limitations
ModSecurity requires security expertise for effective deployment and tuning. Organizations without dedicated security resources may struggle with rule configuration and false positive management.
The platform operates at the HTTP layer and cannot protect against all application vulnerabilities. Code-level vulnerabilities requiring deeper analysis benefit from complementary SAST tools or IAST tools alongside WAF protection.
As an open-source project, ModSecurity doesn’t include commercial support unless purchased separately. Organizations requiring guaranteed support SLAs should consider commercial WAF offerings or managed security services.
Performance tuning may be necessary for high-traffic applications. Complex rule sets with extensive pattern matching can impact request processing latency requiring careful optimization.
