Mend SAST is a commercial SAST tool from Mend.io, the company formerly known as WhiteSource. It scans 25 programming languages using taint analysis and ships with an MCP server that plugs directly into AI coding assistants like Cursor, Claude Code, and GitHub Copilot.
Mend.io was founded in 2011 in Israel and rebranded from WhiteSource in May 2022. The company has raised roughly $125M in funding, backed by Pitango Growth and M12 (Microsoft’s venture fund).
Forrester named Mend a Strong Performer in their Q3 2025 SAST Wave, with top scores in the innovation and triage criteria.
What is Mend SAST?
Mend SAST uses taint analysis to trace the flow of untrusted data through your code. It tracks three things: where tainted data enters (sources like HTTP parameters and file reads), where it gets cleaned (sanitizers), and where unsanitized data could cause damage (sinks like SQL queries or command execution).
The tool runs two engine generations. Gen 1 covers all 25 languages.
Gen 2 adds deeper cross-file analysis for Java, C#, Python, JavaScript/TypeScript, and C/C++.
Gen 2 engines offer three scan profiles: Fast (prioritizes speed), Balanced (optimizes between speed and detection), and Deep (no analysis limits, longest duration).
The “Agentic SAST” capability is the main differentiator. As developers use AI coding assistants, Mend’s MCP server scans generated code before it hits the repository.
The MCP server exposes two tools: mend-code-security-assistant for SAST and mend-dependencies-assistant for SCA.
MCP server integrates with Cursor, Windsurf, Claude Code, GitHub Copilot, Amazon Q, and Gemini CLI. Scans AI-generated code for CWEs and dependencies for CVEs.
The agent can iterate up to 3 times to fix issues.
Key features
| Feature | Details |
|---|---|
| Languages | 25 (Java, C#, Python, JS/TS, Go, Kotlin, PHP, Ruby, Rust, Swift, C/C++, ABAP, APEX, COBOL, and more) |
| Analysis type | Taint analysis (source → sanitizer → sink tracking) |
| Engine generations | Gen 1 (all languages) and Gen 2 (Java, C#, Python, JS/TS, C/C++) |
| Scan profiles | Fast, Balanced, Deep (Gen 2 only) |
| CWE coverage | 70+ CWE types |
| Scan types | Full, Incremental, Secrets detection |
| Report formats | SARIF, HTML, PDF, JSON, CSV, XML |
| Compliance | OWASP 2017/2021/2025, PCI DSS 3.2/4.0, HIPAA, HITRUST, NIST, SANS, MISRA C/C++ |
| CLI command | mend code (replaces legacy mend sast) |
| Timeouts | 480 min per language, 60s–1800s per file |
Taint analysis and data flow tracking
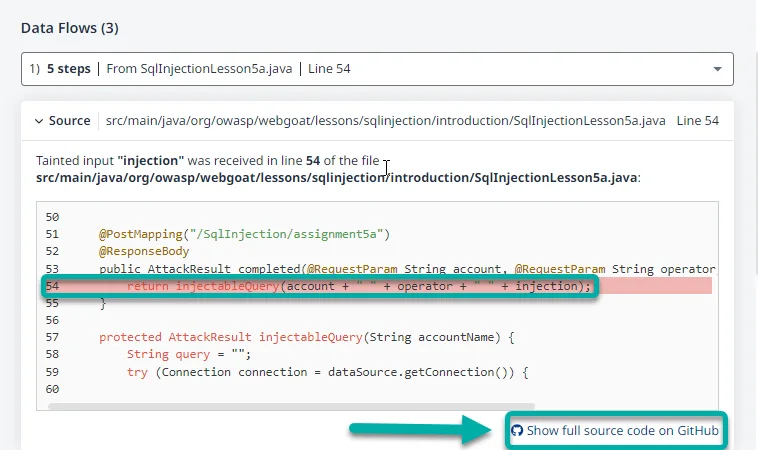
Mend traces tainted data from entry points through your codebase. Sources include HTTP request parameters, file reads, command-line arguments, and network services.
Predefined sanitizers are built in, and you can add custom ones for your own validation functions.
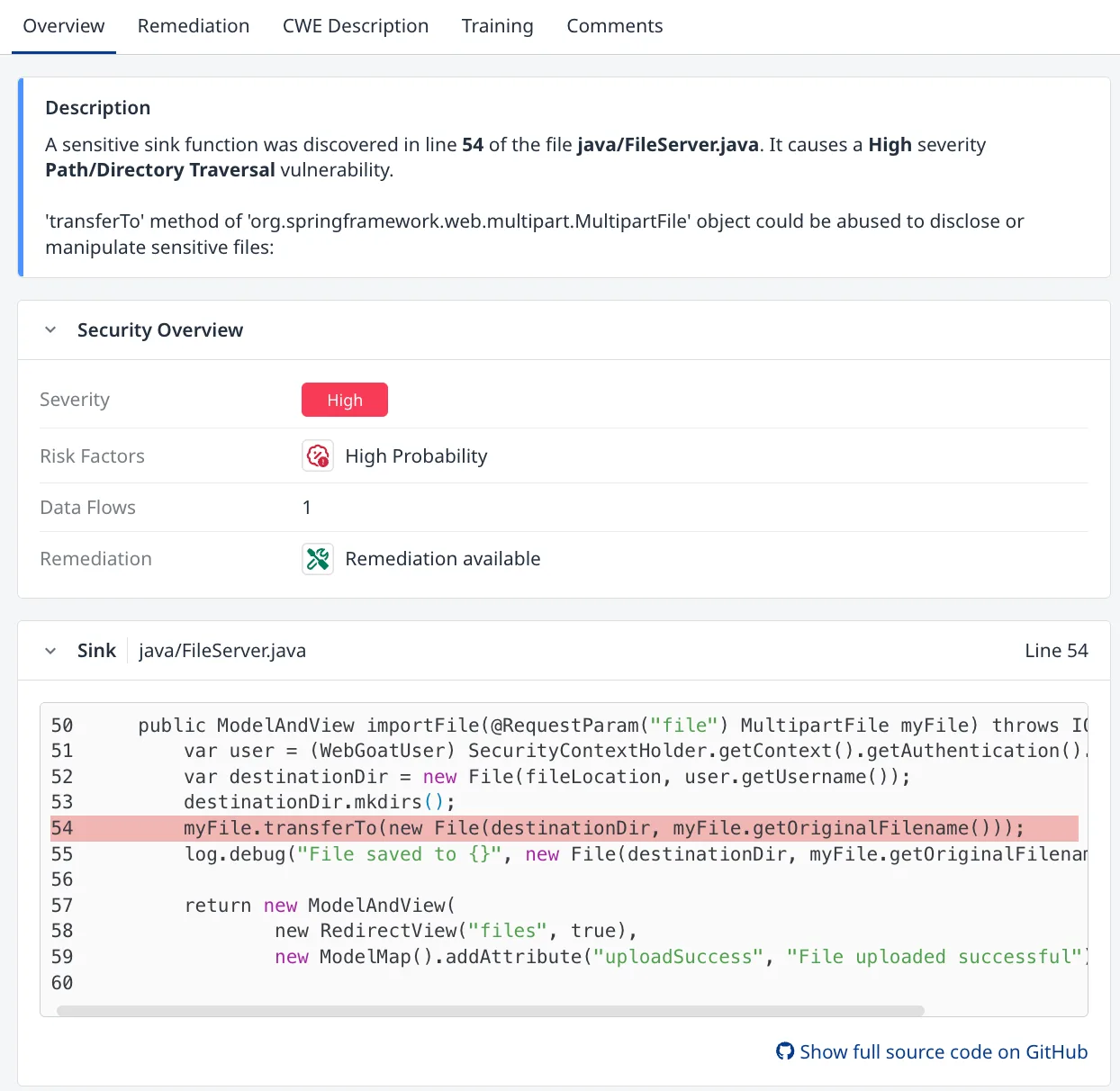
Reachability analysis filters out findings where vulnerable code paths are not actually exercised in your application. This helps separate exploitable issues from theoretical ones.
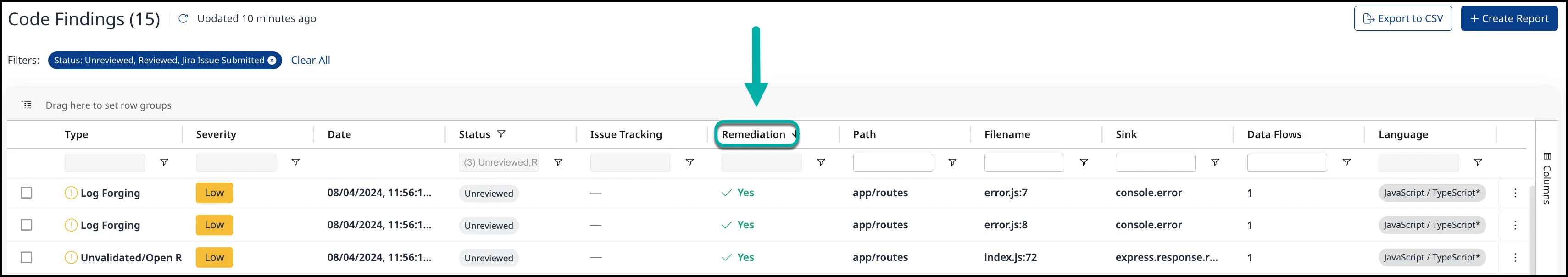
Finding triage and remediation
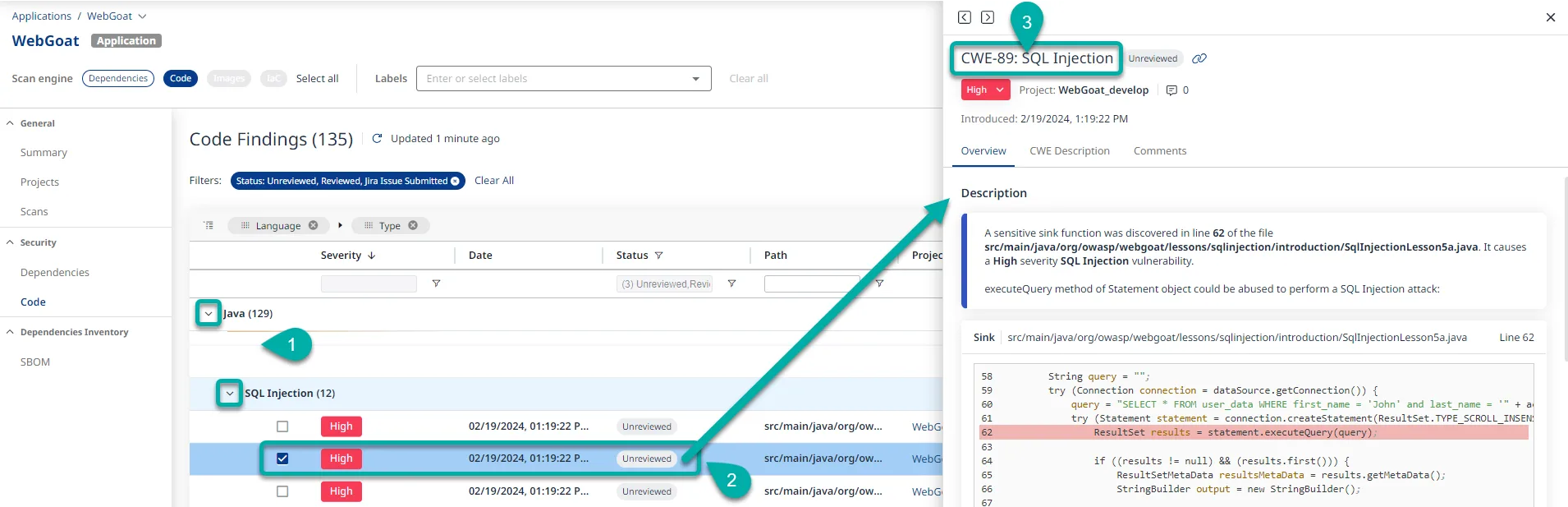
Each finding includes CWE classification, severity rating, data flow paths, and the exact source code location. The platform tracks remediation status across findings and lets you filter by severity, language, CWE type, or status.
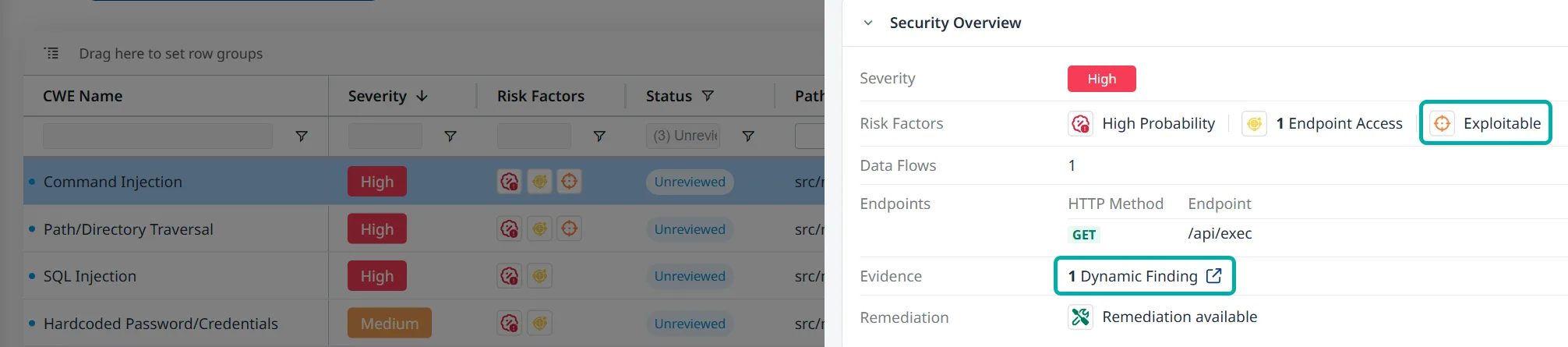
SAST and DAST correlation
When you run both Mend SAST and DAST against the same application, findings correlate automatically. A static code vulnerability confirmed by dynamic testing gets marked as “Exploitable,” which helps prioritize what to fix first.
Agentic IDE integration
The MCP server is what sets Mend apart from most SAST tools right now. It works with:
- Cursor
- VS Code (via Copilot)
- Claude Code
- Windsurf
- Amazon Q Developer
- Gemini CLI
- Gemini Code Assist
- Antigravity
When an AI agent generates code, the MCP server checks it for security issues and returns remediation guidance. The agent can iterate up to three times to produce secure code.
For dependencies, it checks CVEs but only flags direct dependencies, not transitive ones.
For traditional IDE use, Mend offers the Advise Code plugin for JetBrains IDEs (IntelliJ IDEA, PyCharm, WebStorm). VS Code and Visual Studio extensions exist but only cover SCA, not SAST.
Scan types
Three scan modes are available:
- Full scan — Analyzes the entire codebase. Use this for initial baselines and periodic deep checks.
- Incremental scan — Only checks changes since the last baseline. Requires a prior full scan with
--upload-baseline. Faster for CI/CD pipelines. - Secrets detection — Pattern-matching for hardcoded credentials, API keys, and tokens in config files (JSON, YAML, XML, .properties, .config). Covers CWE-798 and CWE-260.
Compliance and reporting
Reports map findings to specific compliance frameworks. You can generate reports in SARIF, HTML, PDF, JSON, CSV, or XML format.
Supported standards: OWASP Top 10 (2017, 2021, 2025), PCI DSS (3.2 and 4.0), HIPAA, HITRUST, NIST, CAPEC, SANS Top 25, and MISRA (C:2025, C++:2023).
Integrations
Getting started
MEND_EMAIL, MEND_USER_KEY, MEND_URL) or command-line parameters.mend code in your project directory. For a specific path, use mend code --dir /path/to/project. Add --secrets-detection to include credential scanning.Set up CI/CD — Add the Mend CLI to your pipeline. GitHub Actions, Azure Pipelines, Bitbucket Pipelines, CircleCI, and Jenkins are all supported.
Use --scope to organize findings by org, app, and project.
mend-code-security-assistant (SAST) and mend-dependencies-assistant (SCA).When to use Mend SAST
Mend SAST fits teams that use AI coding assistants and want security scanning wired into the code generation loop. The MCP server integration with Cursor, Claude Code, and Copilot is something most SAST tools do not offer yet.
Teams already on Mend SCA get a unified dashboard where first-party code vulnerabilities sit next to third-party dependency issues. The hybrid architecture keeps source code on-premises while using cloud analysis for reporting and policy enforcement.
For teams that want open-source SAST or don’t use AI coding assistants, Semgrep CE or SonarQube are better starting points. If you need a SAST tool that runs entirely in your own infrastructure with no cloud dependency, look at Checkmarx or Fortify.
Note: Formerly WhiteSource (rebranded May 2022). Forrester Strong Performer in SAST Wave Q3 2025.