Jadx is a widely used Android APK decompiler with over 47,300 GitHub stars.
Developed by skylot, it is a go-to tool for Android security researchers, developers, and reverse engineers who need to examine compiled Android applications.
The tool converts Dalvik bytecode (DEX format) back into readable Java source code with high accuracy.
Unlike traditional workflows that required multiple tools chained together, Jadx provides an integrated solution with both graphical and command-line interfaces. Its fast multi-threaded decompilation engine handles modern Android apps efficiently, making it invaluable for security assessments and code analysis.
What is Jadx?
Jadx is a Dex to Java decompiler that processes Android APK files and produces readable Java source code. The decompilation process reverses the compilation that happens when Android apps are built, transforming the optimized bytecode back into human-readable Java that closely resembles the original source.
The tool excels at handling complex Android code patterns including lambda expressions, try-with-resources, and other modern Java features. This makes the decompiled output significantly more readable than older decompilers that struggled with these constructs.
Jadx-GUI provides a complete IDE-like interface for browsing decompiled code, navigating between classes, searching for strings and methods, and examining AndroidManifest.xml and resource files. The command-line tool (jadx) enables batch processing and integration into automated workflows, making it suitable for CI/CD pipelines and large-scale analysis.
Key features
Decompilation Quality
Jadx produces high-quality Java source code that is often compilable or very close to it. The decompiler handles complex control flow, reconstructs variable names where possible, and properly represents Android-specific patterns like ContentProvider implementations and BroadcastReceivers.
The tool includes sophisticated algorithms for handling obfuscated code. While it cannot reverse obfuscation completely, it produces the most readable output possible and supports loading ProGuard/R8 mapping files to restore original names when available.
User Interface
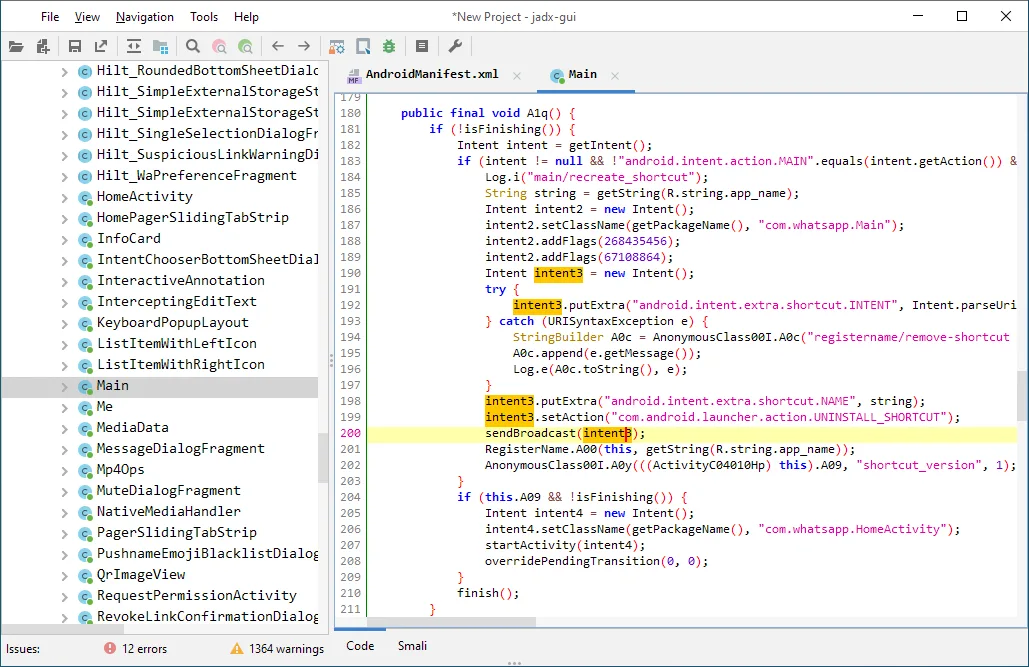
Jadx-GUI provides a comprehensive environment for analyzing decompiled code. You can browse the class hierarchy, view decompiled Java alongside smali bytecode, search for strings and identifiers across the entire codebase, and navigate through cross-references to understand code relationships.
The interface includes syntax highlighting, code folding, and find/replace functionality. You can bookmark important classes, export individual files or entire projects, and manage multiple APKs simultaneously in tabbed windows.
Integration with Mobile Security Tools
Security researchers combine Jadx with other mobile security tools for comprehensive analysis. After decompiling with Jadx, you might use Frida for runtime instrumentation, mitmproxy for traffic analysis, or Ghidra for deeper binary analysis of native libraries.
The tool works seamlessly in security testing workflows. Decompile the APK with Jadx to understand authentication logic, then use that knowledge to craft Frida hooks that bypass security controls or intercept sensitive API calls.
Command-Line Automation
The jadx command-line tool enables scripting and automation. You can batch-process multiple APKs, integrate decompilation into continuous security scanning pipelines, or export specific classes for focused analysis. Options control output format, resource processing, and deobfuscation behavior.
When to use Jadx
Strengths:
- Most actively maintained Android decompiler with regular updates
- Highest quality decompilation output available for Android apps
- User-friendly GUI requires minimal learning curve
- Handles modern Android code patterns and Java language features
- Fast decompilation even for large enterprise applications
- Completely free and open source with permissive licensing
- Strong community support and extensive documentation
- Cross-platform (Windows, macOS, Linux)
Limitations:
- Cannot decompile native code (use Ghidra for .so libraries)
- Heavily obfuscated or protected apps may produce unclear output
- Decompiled code may not be 100% identical to original source
- Some compile-time optimizations are not reversible
- Resource-intensive for extremely large APKs (500MB+)
Getting started
jadx-gui for the graphical interface or jadx from the command line.jadx -d output_directory app.apk from the command line to save decompiled sources. Add --export-gradle to create an importable Gradle project structure, or use --deobf to apply deobfuscation heuristics.Combine Jadx with Objection for rapid security testing: decompile with Jadx to identify interesting methods, then hook them at runtime with Objection to observe and manipulate behavior.