Invicti ASPM is a commercial Application Security Posture Management platform that pairs proof-based DAST scanning with multi-scanner orchestration. Invicti acquired Kondukto in August 2025 and merged both products. The platform connects over 110 security tools, CI/CD systems, and issue trackers. Invicti claims 99.98% accuracy on its DAST findings through safe exploitation proofs, and reports 40% shorter remediation times across 3,600+ organizations.
The platform doesn’t replace your existing scanners. It orchestrates them. Results from SAST, SCA, DAST, container scanning, and IaC tools get pulled in, normalized, deduplicated, and routed through automated workflows. Verified fixes trigger targeted rescans that close tickets without anyone stepping in.
Invicti started as Netsparker, a DAST tool known for proof-based scanning. Kondukto was a Turkish-founded ASPM startup with broad scanner support and a CLI tool. After the acquisition, both products merged under the Invicti ASPM brand. The company is headquartered in Austin, Texas.
What is Invicti ASPM?
Invicti ASPM is a commercial ASPM platform that orchestrates your security testing pipeline. It sits on top of your existing scanners, pulling in results from SAST, SCA, DAST, container scanning, and IaC tools, then normalizing everything into one view.
The main differentiator compared to ArmorCode or DefectDojo is the proof-based scanning layer from Invicti’s DAST engine. When the built-in DAST scanner finds a potential vulnerability, it performs a safe exploitation to confirm the flaw actually exists. You get a proof artifact attached to every finding, not just a confidence score.
Key features
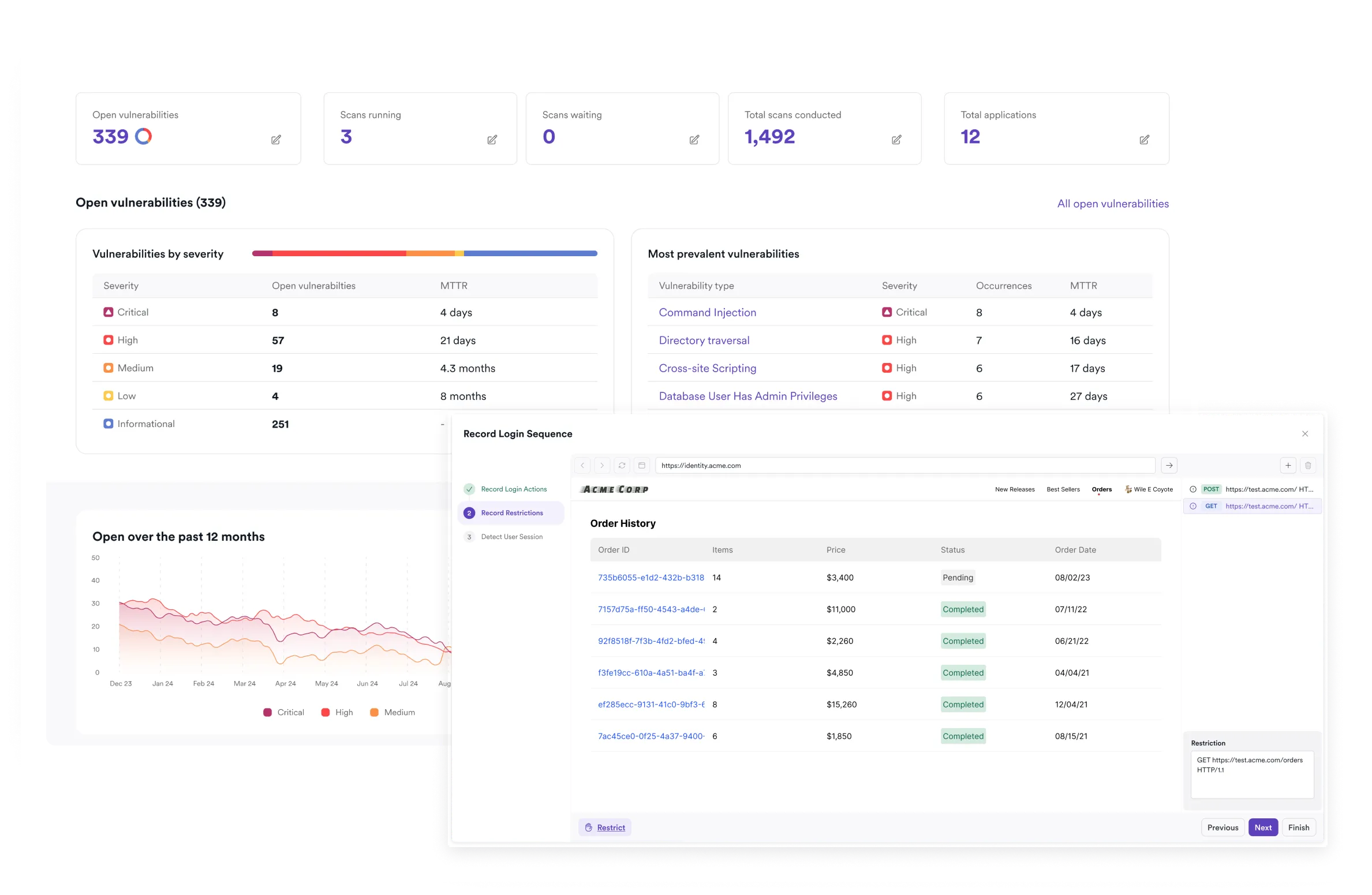
Proof-based scanning
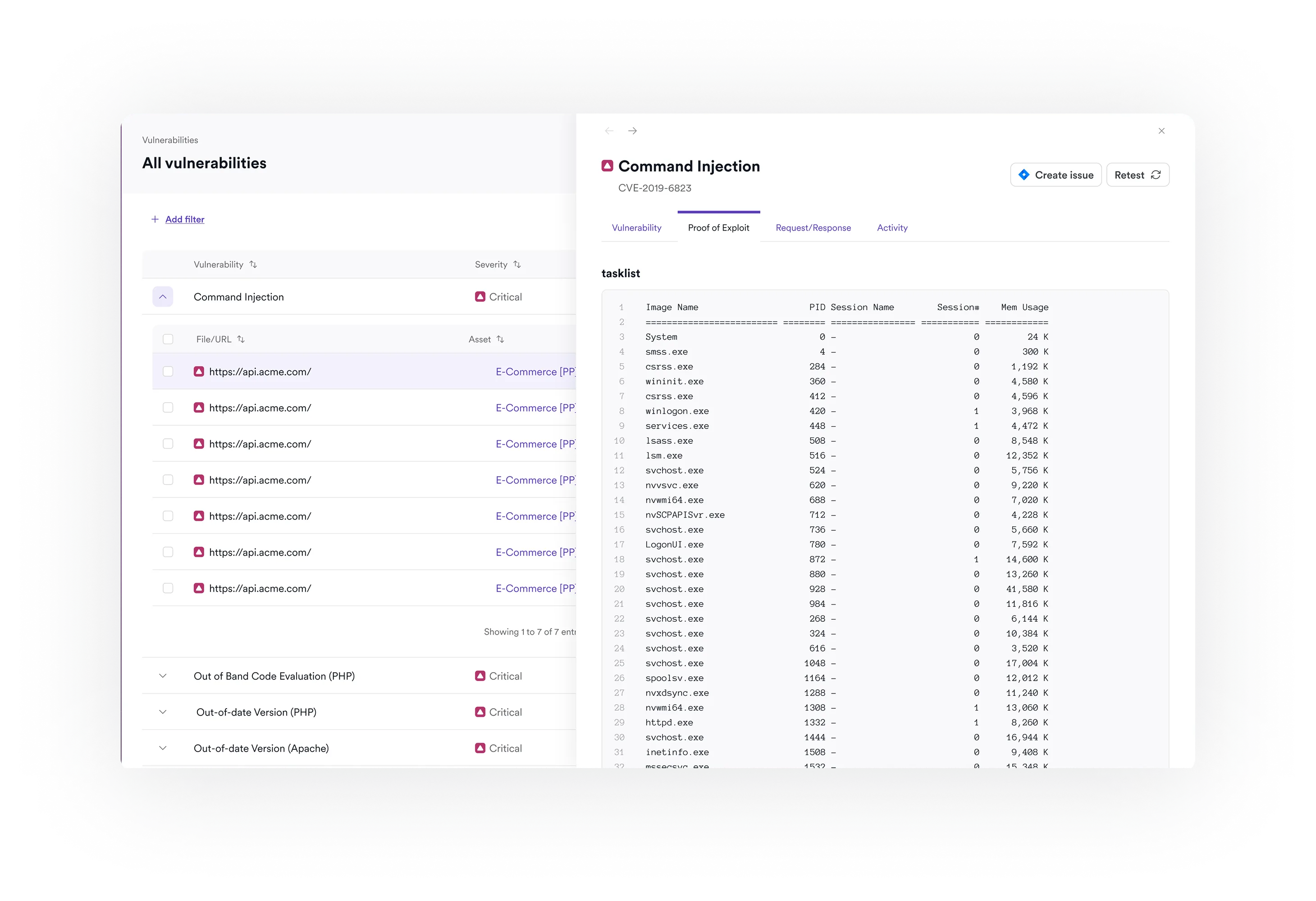
The built-in DAST engine validates each finding through safe exploitation before reporting it. If the scanner detects a potential SQL injection, it attempts a read-only query to prove the flaw exists. A suspected remote file inclusion gets confirmed by reading a system file. Each confirmed vulnerability includes a proof artifact showing how the issue was exploited. Invicti reports this as 99.98% scan accuracy, close to zero false positives in practice.
Security orchestration
Invicti ASPM manages the scan lifecycle from trigger to ticket. You define which scanners run against which projects, set vulnerability thresholds, and configure automated ticket creation. Supported scanner and tool categories:
| Category | Tools |
|---|---|
| SAST | Semgrep, SonarQube, Checkmarx, Fortify, CodeQL, Veracode, Coverity, Brakeman, Gosec, SonarCloud |
| SCA | Snyk, Trivy, Dependabot, OWASP Dependency-Check, Mend.io |
| DAST | Invicti (native), Burp Suite, OWASP ZAP, Acunetix |
| Container | Trivy, Grype, Docker Scout |
| IaC | Checkov, KICS, Terrascan, tfsec |
| CSPM | Cloud security posture checks |
| Bug Bounty | Bug bounty platform integration |
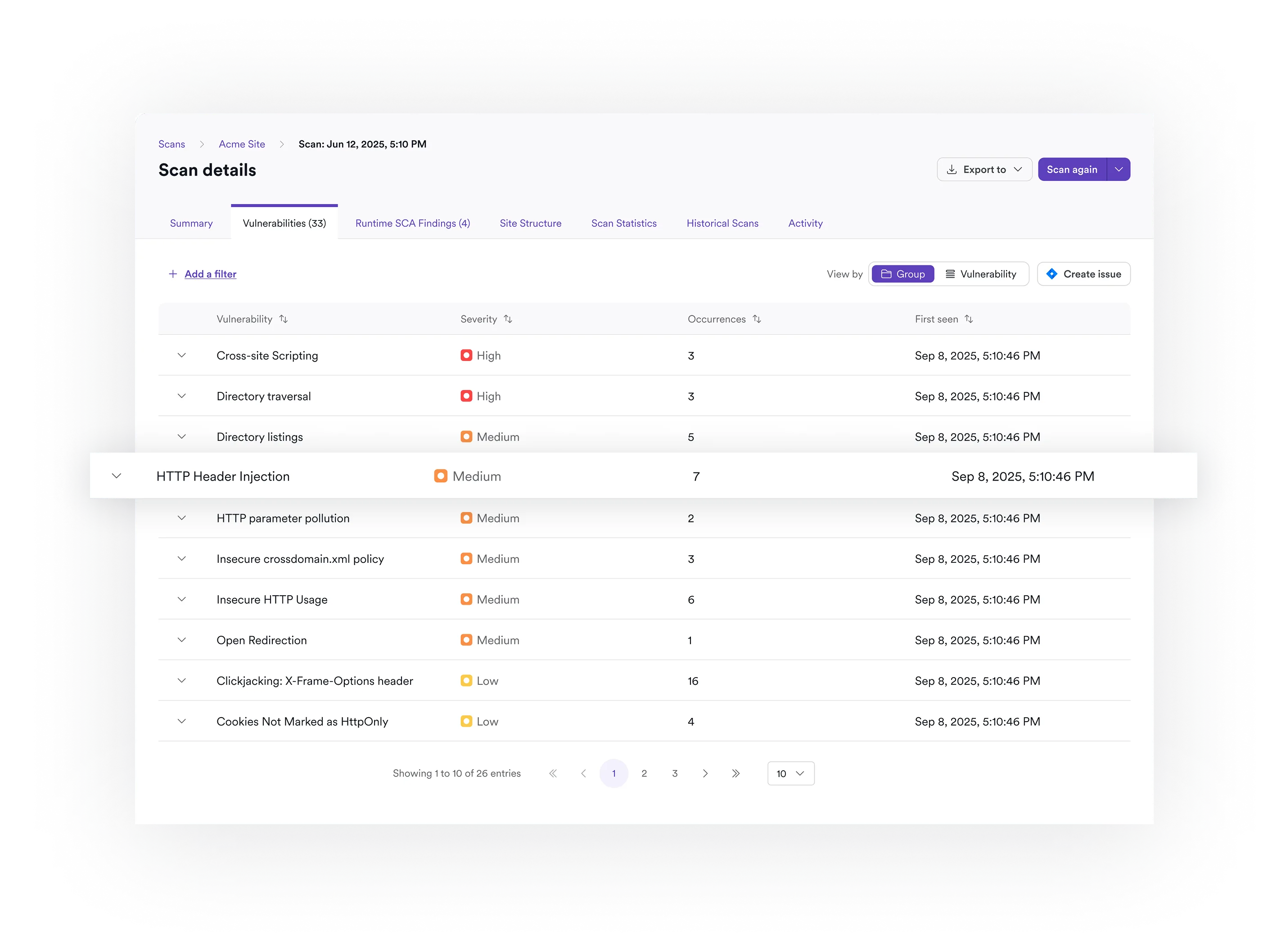
Deduplication and normalization
Run three scanners against the same codebase and you’ll get overlapping findings. Invicti ASPM normalizes results into a common format, merges duplicates, and applies suppression rules for known false positives or accepted risks. If you’ve spent a morning deduplicating Checkmarx and Semgrep results in a spreadsheet, this is the part that saves you.
Fix verification
After a developer pushes a fix, Invicti ASPM triggers a targeted rescan against that specific finding. If the vulnerability is gone, the ticket closes automatically. If it’s still there, the ticket reopens with updated context. No more pinging the security team to re-run a scan and manually close Jira tickets.
SBOM Radar
SBOM Radar tracks every component in your applications: libraries, frameworks, transitive dependencies. It watches for newly disclosed CVEs against your bill of materials and flags license compliance risks. You can import SBOMs in CycloneDX or SPDX format, or let integrated SCA scanners generate them.
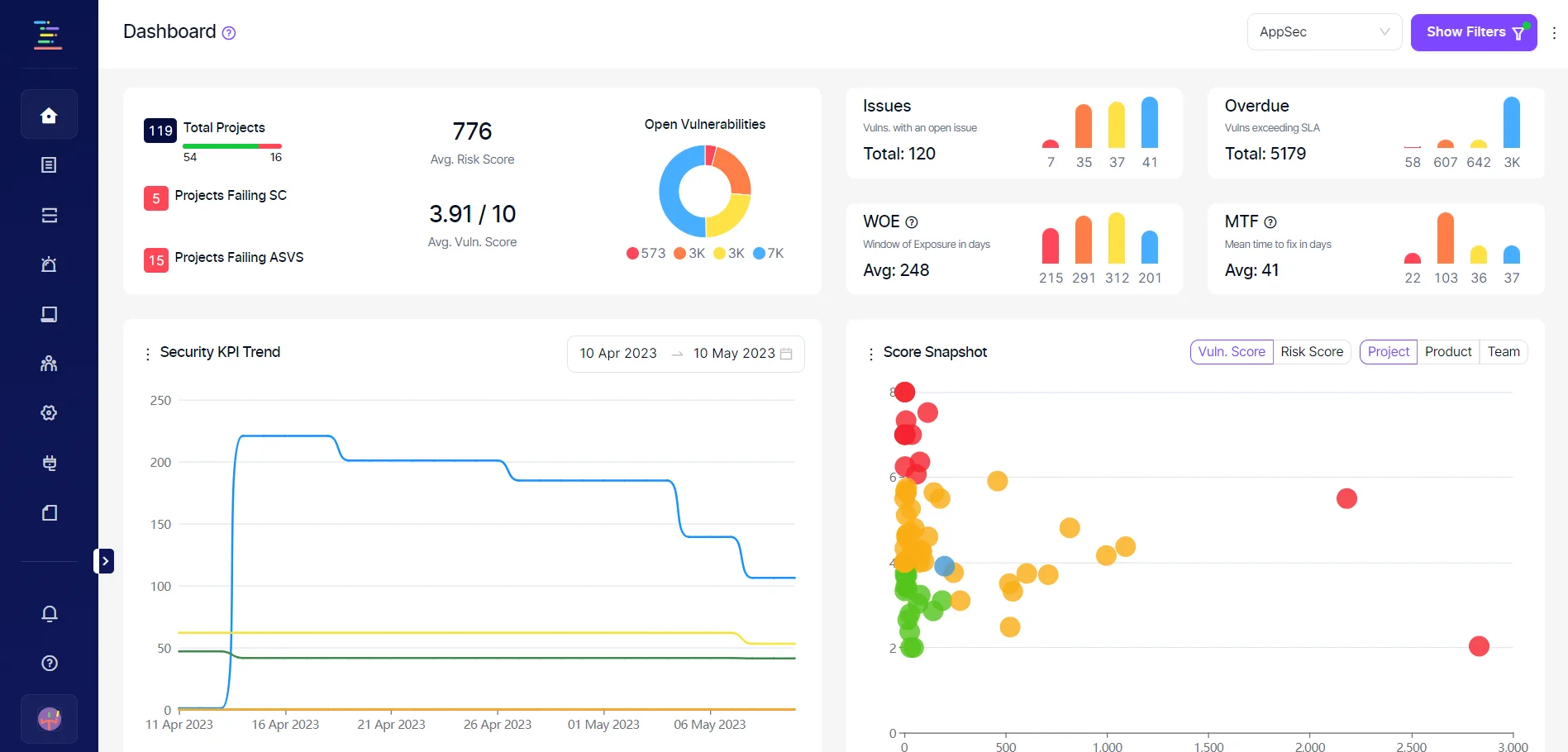
Security KPI dashboard
The dashboard tracks security KPIs: mean time to fix (MTF), window of exposure (WOE), vulnerability density, and risk score trends. You can filter metrics by project, product, business unit, team, or label. Security scoring at the developer and team level shows where training or process changes would help.
Integrations
Invicti ASPM integrates with 110+ tools across multiple categories:
Getting started
curl -sSL https://cli.kondukto.io | shINVICTI_ASPM_HOST and INVICTI_ASPM_TOKENkdt scan -p ProjectName -t semgrep -b main to kick off a scan and see results flow into the dashboard.CLI tool (KDT)
The KDT CLI is how you integrate Invicti ASPM into your CI/CD pipelines. It’s written in Go and open-source under GPL-3.0.
curl -sSL https://cli.kondukto.io | sh
export INVICTI_ASPM_HOST=https://your-instance.invicti.com
export INVICTI_ASPM_TOKEN=your_api_token
Commands
| Command | Description |
|---|---|
kdt ping | Check server connectivity |
kdt ping -a | Validate API token |
kdt scan -p Project -t semgrep -b main | Trigger a scan |
kdt scan ... --threshold-crit 0 --threshold-high 5 | Scan with vulnerability thresholds |
kdt scan ... -f results.json | Import results from file |
kdt scan ... --async | Non-blocking scan |
kdt scan ... --image myapp:latest | Container image scan |
kdt scan ... -M main --pr-number 42 | PR decoration scan |
kdt release -p Project -b main --sast --sca | Check release criteria |
kdt sbom import -f sbom.json -p Project -b main | Import SBOM |
kdt list projects | List all projects |
kdt list scanners | List available scanners |
kdt list agents | List registered agents |
kdt create project -p Name --repo-id URL --alm-tool github | Create a project |
Exit codes: 0 = success, 1 = error, 100 = unauthorized, 255 = threshold exceeded.
GitHub Actions
- name: Security Scan
env:
INVICTI_ASPM_HOST: ${{ secrets.INVICTI_ASPM_HOST }}
INVICTI_ASPM_TOKEN: ${{ secrets.INVICTI_ASPM_TOKEN }}
run: |
curl -sSL https://cli.kondukto.io | sh
kdt scan -p ${{ github.repository }} -t semgrep -b ${{ github.ref_name }} --threshold-crit 0
GitLab CI
security_scan:
stage: test
script:
- curl -sSL https://cli.kondukto.io | sh
- kdt scan -p $CI_PROJECT_NAME -t trivy -b $CI_COMMIT_REF_NAME --threshold-crit 0
variables:
INVICTI_ASPM_HOST: $INVICTI_ASPM_HOST
INVICTI_ASPM_TOKEN: $INVICTI_ASPM_TOKEN
Jenkins Pipeline
stage('Security Scan') {
environment {
INVICTI_ASPM_HOST = credentials('invicti-aspm-host')
INVICTI_ASPM_TOKEN = credentials('invicti-aspm-token')
}
steps {
sh 'curl -sSL https://cli.kondukto.io | sh'
sh 'kdt scan -p my-project -t checkmarx -b ${BRANCH_NAME} --threshold-crit 0'
}
}
Deployment
| Option | Specs |
|---|---|
| Cloud (SaaS) | Fully managed, no infrastructure |
| On-Premise (PoC) | 4 cores, 16GB RAM, 90GB disk |
| On-Premise (Prod) | 8 cores, 64GB RAM, 250GB disk |
| Distributed | App: 4c/64GB, DB: 8c/64GB (MongoDB 5+) |
When to choose Invicti ASPM
Invicti ASPM fits best when you’re running multiple security scanners and tired of manually reconciling their output.
Strengths:
- Proof-based scanning eliminates false positives from the DAST layer
- 110+ integrations, so it probably works with whatever you already run
- Fix verification closes the loop on remediation without manual rescans
- PR decoration and release gates put security checks where developers already work
- Security KPI dashboards track MTTR, window of exposure, and risk score trends
Limitations:
- Commercial-only, no free tier. If budget is tight, DefectDojo is the open-source alternative
- Proof-based scanning only applies to the DAST engine. Findings from third-party SAST/SCA tools still depend on those tools’ accuracy
How it compares:
| vs. | Key difference |
|---|---|
| DefectDojo | Open-source aggregation without proof-based scanning or built-in DAST |
| ArmorCode | Cloud-only; Invicti ASPM supports on-premise deployment and uses proof-based scanning |
| Apiiro | Focuses on code-change risk analysis; Invicti covers the full scan orchestration pipeline |
| Ox Security | Supply-chain focus; Invicti covers a wider range of scanner integrations |
History
Invicti started as Netsparker, a DAST tool known for proof-based scanning. Kondukto was a Turkish-founded ASPM startup that built an orchestration platform with broad scanner support and a solid CLI.
Invicti acquired Kondukto in August 2025 and merged both products under the Invicti ASPM brand. The KDT CLI still uses the Kondukto domain (cli.kondukto.io) for downloads, but the environment variables were rebranded to INVICTI_ASPM_HOST and INVICTI_ASPM_TOKEN.
Note: Formed from Invicti's acquisition of Kondukto in August 2025. Combines Invicti's proof-based DAST with Kondukto's ASPM orchestration.

Comments
Powered by Giscus — comments are stored in GitHub Discussions.