Gitleaks is an open-source secret scanner designed to detect and prevent hardcoded secrets in git repositories. Maintained by Zach Rice and the Gitleaks community, it has over 24,400 GitHub stars and is one of the most widely adopted SAST tools for secret detection.
According to the 2024 Verizon Data Breach Investigations Report, stolen credentials remain one of the top initial access vectors for breaches. Security teams pick Gitleaks for its speed, accuracy, and low false positive rate compared to entropy-only scanners.
What is Gitleaks?
Gitleaks scans git repositories, files, directories, and stdin to find exposed API keys, passwords, tokens, and other sensitive data. The tool uses regex patterns and entropy detection to identify secrets that developers accidentally commit to version control.
Unlike full-featured SAST platforms, Gitleaks focuses exclusively on secret detection. This specialization makes it faster and easier to integrate into existing development workflows.
You can run it locally as a pre-commit hook, in CI/CD pipelines, or as a GitHub Action to scan pull requests automatically.
Gitleaks generates reports in multiple formats including JSON, CSV, JUnit, and SARIF. The SARIF output integrates with GitHub Advanced Security, allowing you to view findings directly in GitHub’s security tab and block pull requests that introduce secrets.
Key features
| Feature | Details |
|---|---|
| CLI commands | git (scan repos), dir (scan directories), stdin (pipe input) |
| Configuration | TOML format (.gitleaks.toml), env vars, or --config flag |
| Output formats | JSON, CSV, JUnit, SARIF, custom Go templates |
| Installation | Homebrew, Docker (DockerHub + ghcr.io), binary releases, from source |
| Composite rules | Primary + auxiliary rules with proximity constraints (v8.28.0+) |
| Baseline support | Skip known findings via baseline reports |
| License | MIT |
| GitHub Action | gitleaks/gitleaks-action@v2 |
Configurable detection rules
Gitleaks ships with built-in rules for common secret patterns (AWS keys, GitHub tokens, Slack webhooks, etc.). Customize rules or add your own regex patterns in a .gitleaks.toml configuration file.
The tool supports allowlists at both rule-specific and global levels to exclude false positives.
Since v8.28.0, composite rules let you combine a primary rule with auxiliary rules that must match within a specified proximity (withinLines, withinColumns). This reduces false positives for patterns that only matter when they appear near related identifiers.
Pre-commit hook protection
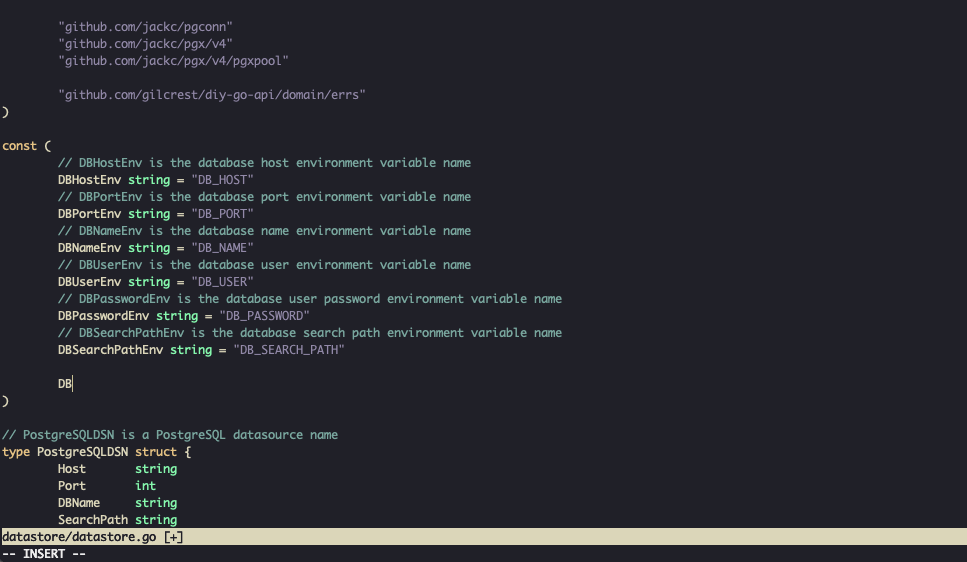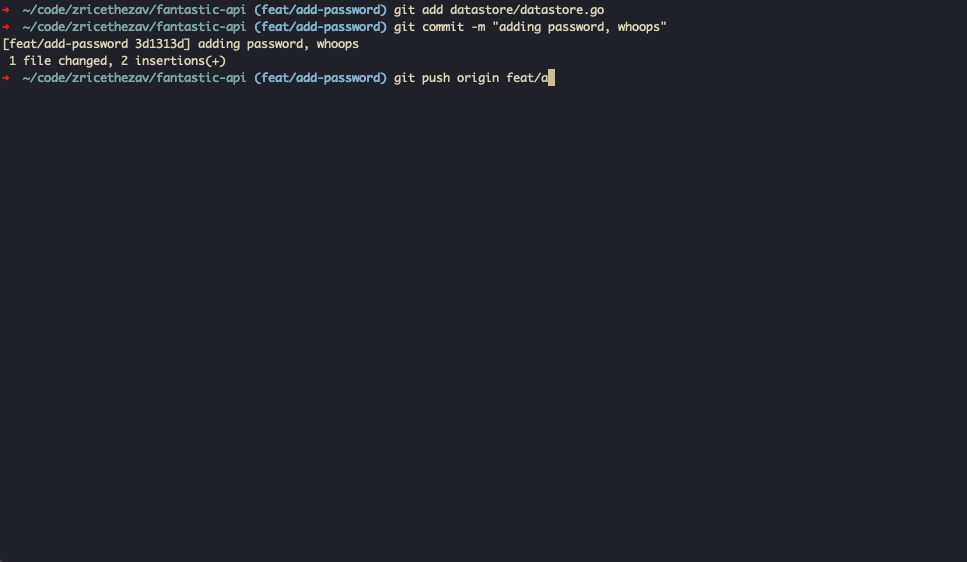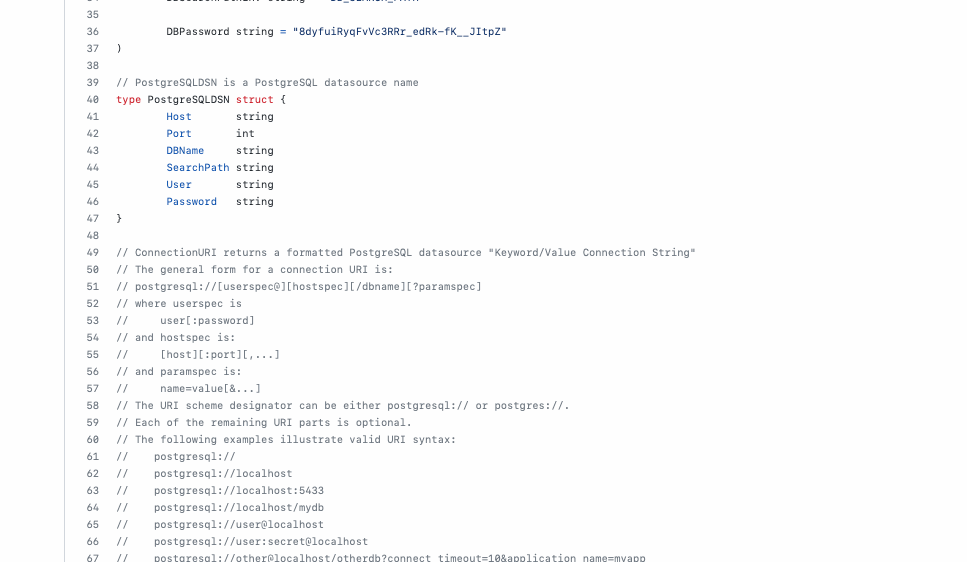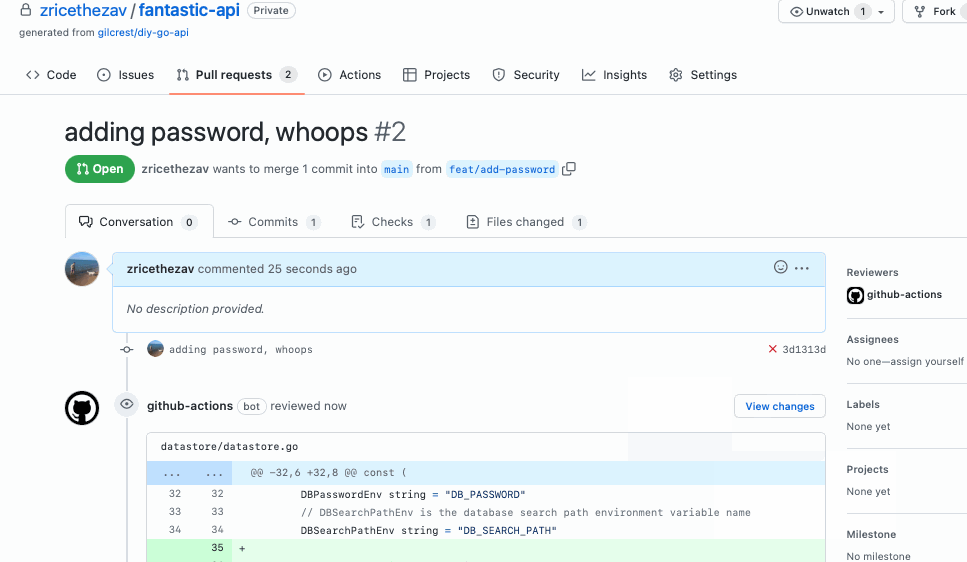
Install Gitleaks as a pre-commit hook to block secrets before they reach your repository. When a developer attempts to commit code containing secrets, Gitleaks stops the commit and displays the offending lines.
Skip the hook temporarily with SKIP=gitleaks git commit when needed.
GitHub Action
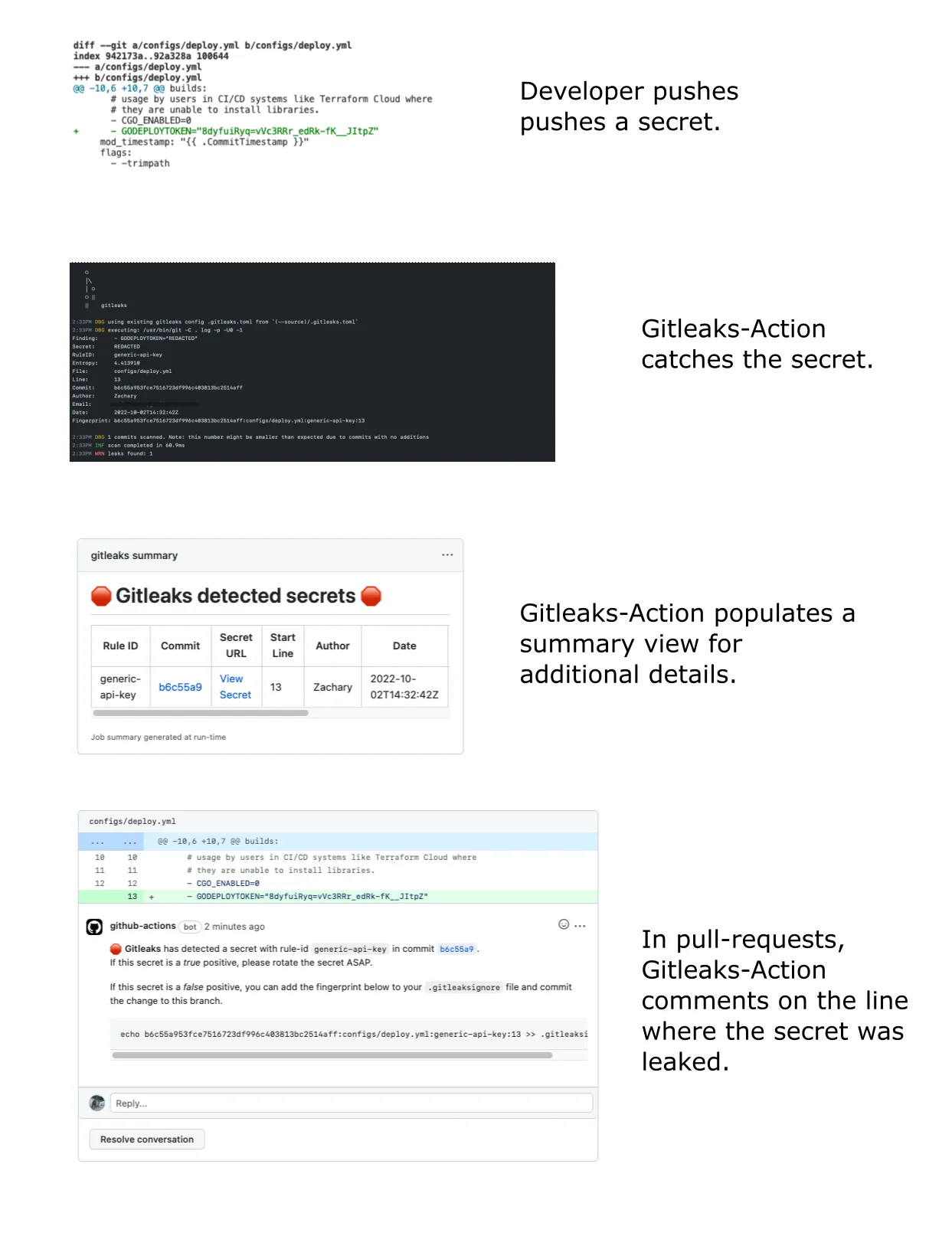
The official gitleaks/gitleaks-action@v2 runs on pull requests and pushes. For organization repositories, a GITLEAKS_LICENSE secret is required.
The action scans changed files and blocks merges when secrets are found.
SARIF output for GitHub integration
Export findings in SARIF format to populate GitHub’s security tab. This puts secret findings alongside CodeQL and Dependabot results in a single view.
Archive and encoding scanning
Gitleaks can scan nested archives (zip, tar, etc.) via --max-archive-depth and recursively decode encoded content with --max-decode-depth. Both default to 0 (disabled) and can be tuned based on your scanning needs.
Getting started
brew install gitleaks on macOS, or pull the Docker image with docker pull zricethezav/gitleaks:latest. Binary releases are available for Linux, macOS, and Windows.gitleaks git -s /path/to/repo to scan git history for secrets. Use gitleaks dir -s /path/to/dir for non-git directories..pre-commit-config.yaml with rev: v8.24.2. Developers get instant feedback before commits reach the repository.--report-path results.json --report-format json to save findings. Upload SARIF output to GitHub Advanced Security with --report-format sarif.When to use Gitleaks
Gitleaks is the go-to choice for teams that want fast, no-frills secret scanning in git repositories. It runs offline, installs as a single binary, and integrates with GitHub Actions out of the box.
For scanning beyond git (Slack, S3, Docker images), TruffleHog covers more ground. For enterprise environments with legacy codebases, detect-secrets offers a baseline approach that avoids upfront remediation.