GitLab SAST provides built-in static application security testing for GitLab repositories. Unlike external SAST tools that require integration, GitLab SAST runs automatically in your CI/CD pipelines with minimal configuration.
For teams already using GitLab, SAST offers a zero-friction security scanning solution with AI-powered features in Ultimate tier.
What is GitLab SAST?
GitLab SAST scans source code for security vulnerabilities on every commit. According to GitLab’s DevSecOps surveys, organizations that shift security left by integrating scanning into CI/CD pipelines detect vulnerabilities significantly earlier in the development lifecycle.
The system uses analyzer containers — Docker images that wrap third-party scanners like Semgrep — to detect issues across multiple programming languages.
When a scan completes, GitLab displays findings directly in merge requests, security dashboards, and vulnerability reports. Developers see security issues alongside other code review feedback without switching tools or platforms.
GitLab Advanced SAST represents the next generation of GitLab’s scanning technology. It provides faster scanning with multi-core support, more accurate detection, and is gradually replacing the legacy Semgrep-based analyzers for all supported languages.
Key features
| Feature | Details |
|---|---|
| Languages (Advanced SAST) | C, C++, C#, Go, Java, JavaScript, Python, Ruby, TypeScript |
| Languages (Standard) | Apex, Elixir, Groovy, Kotlin, Objective-C, PHP, Scala, Swift |
| Analyzers | Advanced SAST, Semgrep, SpotBugs, Kubesec, PMD Apex, Sobelow |
| CI template | include: template: Jobs/SAST.gitlab-ci.yml |
| Default excluded paths | spec, test, tests, tmp |
| Search depth | 20 (Semgrep), 4 (others) |
| Runner requirement | Linux (Docker or Kubernetes executor, amd64 only) |
| FIPS support | Available via -fips image suffix |
Automatic scanning on every commit
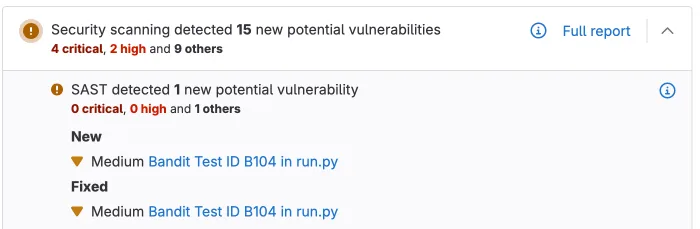
Add GitLab SAST to your project by including the SAST.gitlab-ci.yml template in your .gitlab-ci.yml file. GitLab automatically runs scans on every commit and merge request.
The scanner detects which languages exist in your repository and runs the appropriate analyzers. You don’t configure language-specific settings.
Tier-based feature availability
| Feature | Free | Premium | Ultimate |
|---|---|---|---|
| Basic SAST scanning | Yes | Yes | Yes |
| JSON report download | Yes | Yes | Yes |
| Advanced SAST engine | No | No | Yes |
| MR widget with findings | No | No | Yes |
| Vulnerability management | No | No | Yes |
| Ruleset customization | No | No | Yes |
| AI false positive detection | No | No | Yes (Duo add-on) |
| Agentic fix generation | No | No | Yes (Duo add-on) |
GitLab Advanced SAST
Advanced SAST is GitLab’s proprietary scanning engine with multi-core scanning enabled by default. Enable it with GITLAB_ADVANCED_SAST_ENABLED: "true" in your CI variables.
It currently supports C, C++, C#, Go, Java, JavaScript, Python, Ruby, and TypeScript. Other languages fall back to the Semgrep-based analyzer.
AI-powered false positive detection
For Ultimate tier users with the GitLab Duo add-on, AI analyzes Critical and High severity SAST vulnerabilities to flag likely false positives. Each finding gets a confidence score and explanation, reducing manual triage time.
Agentic SAST vulnerability resolution
Also in Ultimate tier with GitLab Duo, agentic SAST automatically generates merge requests that fix High and Critical severity vulnerabilities. The AI uses multi-shot reasoning to understand code context and create fixes that preserve functionality.
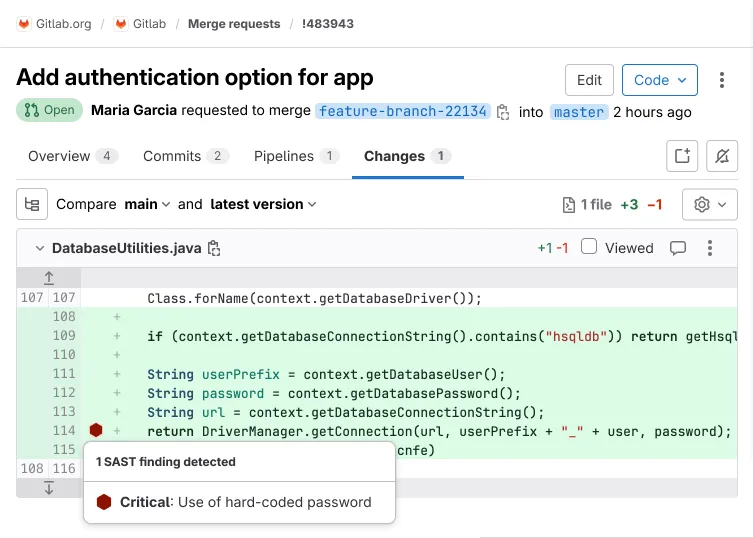
Vulnerability tracking
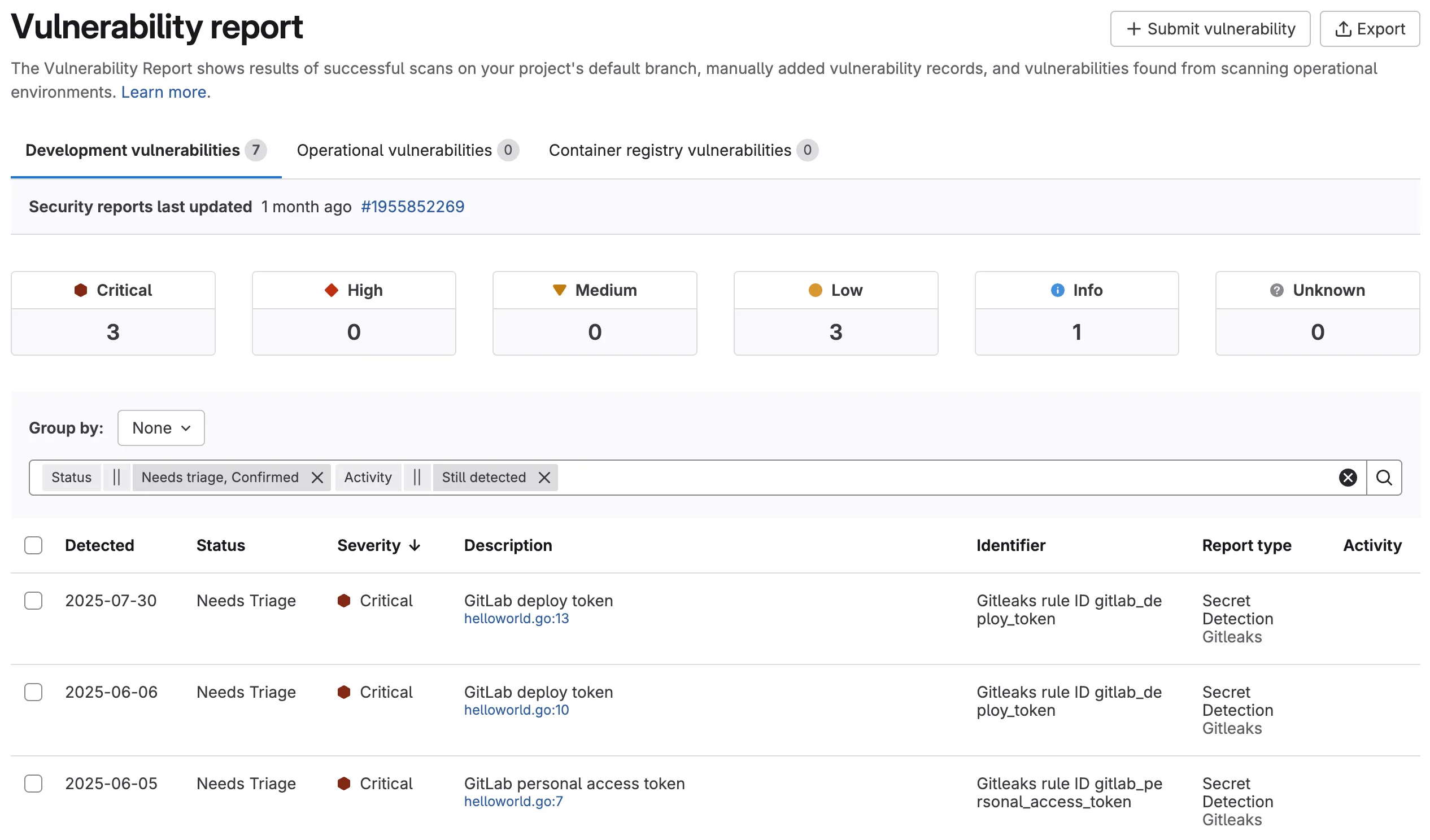
GitLab tracks vulnerabilities across refactoring. If code moves to a different file or line, the vulnerability follows it rather than creating a duplicate. Vulnerabilities also auto-resolve when their associated rules are disabled.
SECURE_ANALYZERS_PREFIX to point to your internal registry.Getting started
include: - template: Jobs/SAST.gitlab-ci.yml to your .gitlab-ci.yml. Make sure you have a test stage defined.SAST_EXCLUDED_PATHS, pin analyzer versions with SAST_ANALYZER_IMAGE_TAG, or enable Advanced SAST with GITLAB_ADVANCED_SAST_ENABLED.When to use GitLab SAST
GitLab SAST is the obvious choice if you’re already on GitLab and want security scanning without adding external tools. The zero-config setup means you can go from nothing to scanning in a single commit.
The real value shows up at the Ultimate tier with GitLab Duo, where AI triage and automatic fix generation cut manual work significantly. Free tier users still get basic scanning and JSON reports, but miss the MR integration and vulnerability management features.
For more customizable scanning outside GitLab, standalone tools like Semgrep or Snyk Code work with any CI/CD system. See our what is SAST guide for a broader overview of static analysis testing.