Falco is a CNCF graduated runtime security tool that detects threats in Kubernetes, containers, and cloud environments by monitoring kernel-level events. Originally created by Sysdig and donated to the CNCF in 2018, Falco reached graduated status in 2024 and has 8.7k GitHub stars with 208 contributors.
The tool runs as a DaemonSet in Kubernetes clusters, capturing system calls through eBPF or a kernel module. It enriches those events with container and Kubernetes metadata, then evaluates them against YAML-based detection rules. Adopters include Shopify, GitLab, Skyscanner, and Booz Allen Hamilton.
What is Falco?
Falco intercepts system calls at the kernel level and checks them against detection rules in real time. Unlike static analysis tools that scan images before deployment, Falco catches threats during execution — containers spawning unexpected shells, processes attempting privilege escalation, applications reading sensitive files like /etc/shadow.
The latest release is v0.43.0 (January 2026). Falco runs on x86_64 and aarch64 architectures and deploys via an official Helm chart. It works with GKE, EKS, and AKS.
Key Features
| Feature | Details |
|---|---|
| Detection engine | eBPF-based kernel syscall monitoring (preferred) or kernel module |
| Rule format | Declarative YAML with macros, lists, and boolean logic |
| Platforms | x86_64 and aarch64 Linux, GKE, EKS, AKS |
| Alert outputs | stdout, files, syslog, program execution, HTTPS endpoints |
| Plugin sources | AWS CloudTrail, GitHub audit logs, Okta events |
| Deployment | Kubernetes DaemonSet via Helm chart |
| CNCF status | Graduated (2024) |
| License | Apache 2.0 |
Detection Rules
Falco’s rules engine uses YAML with conditions, outputs, and priority levels. Rules fire on specific syscall patterns — for example, detecting when a container spawns a shell process or when someone modifies files in /etc, /usr/bin, or /usr/sbin.
The rule syntax supports macros (reusable condition fragments), lists (sets of values), and complex boolean logic. Teams can tune rules to reduce false positives or add detection logic specific to their applications.
Kubernetes Context
Falco enriches kernel events with Kubernetes metadata like pod names, namespaces, labels, and service accounts.
When a rule fires, the alert includes which pod triggered it, what namespace it runs in, and who owns it.
This context makes incident response faster because you immediately know the blast radius.
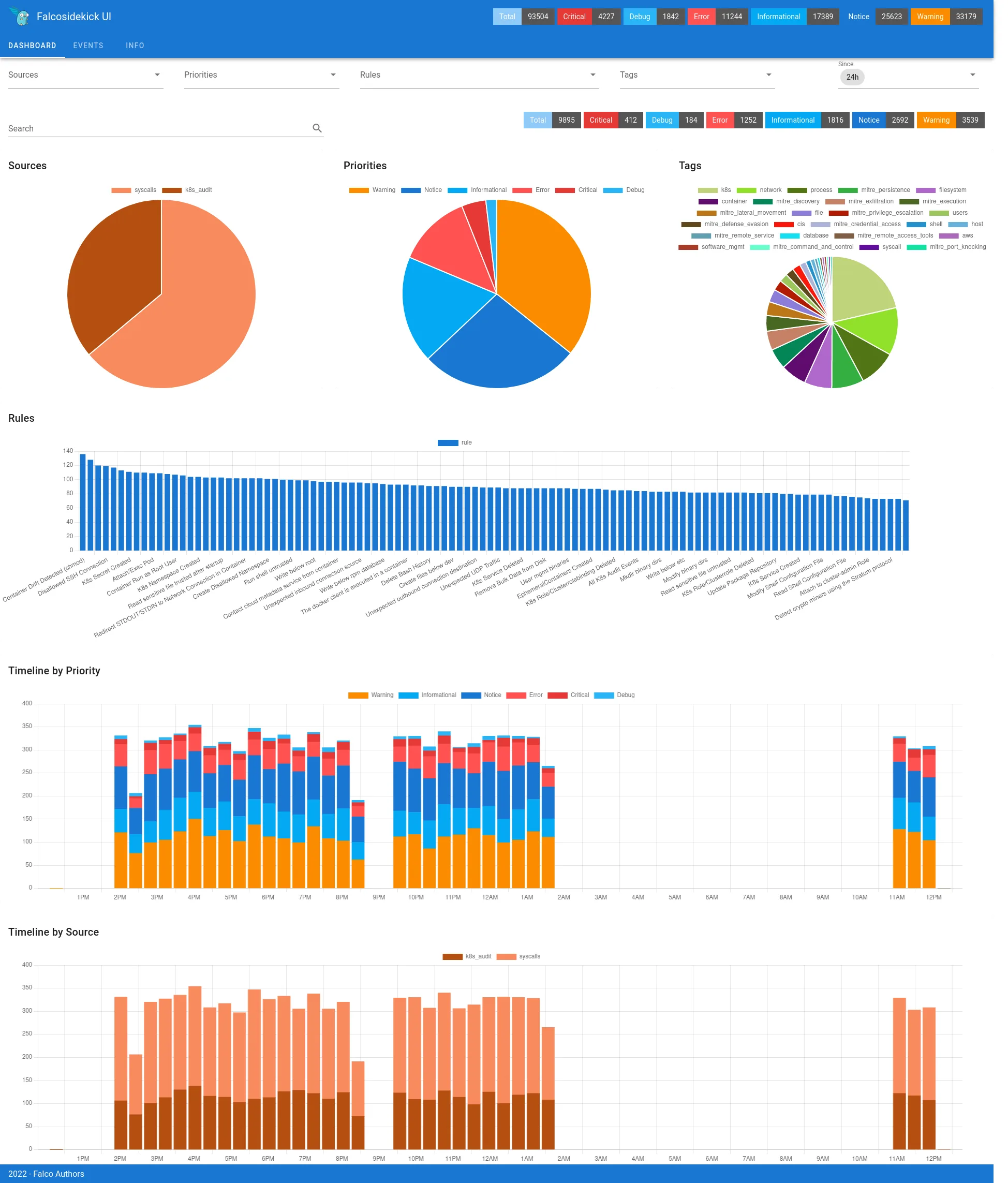
Plugin System
Falco extends beyond kernel monitoring through plugins. Plugins pull events from cloud APIs, parse audit logs, or integrate custom telemetry.
This turns Falco into a detection engine for cloud environments, not just containers.
Current plugins cover AWS CloudTrail for cloud API activity, GitHub audit logs for repository events, and Okta for identity-related threats.
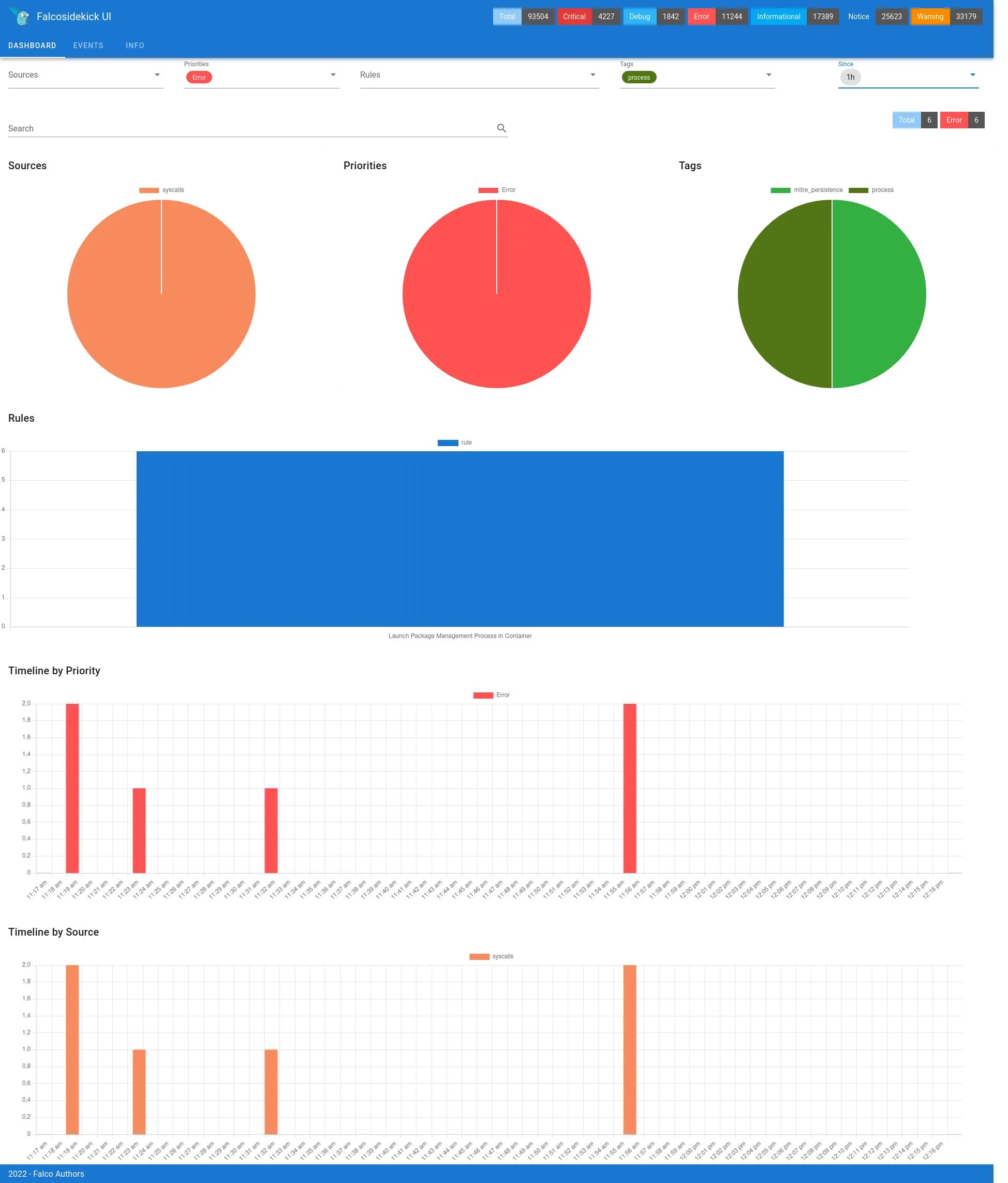
Alert Output
Falco supports five alert delivery mechanisms: standard output, file logging, syslog, program execution, and HTTPS endpoints. JSON-formatted alerts make integration with SIEM systems and data lakes straightforward.
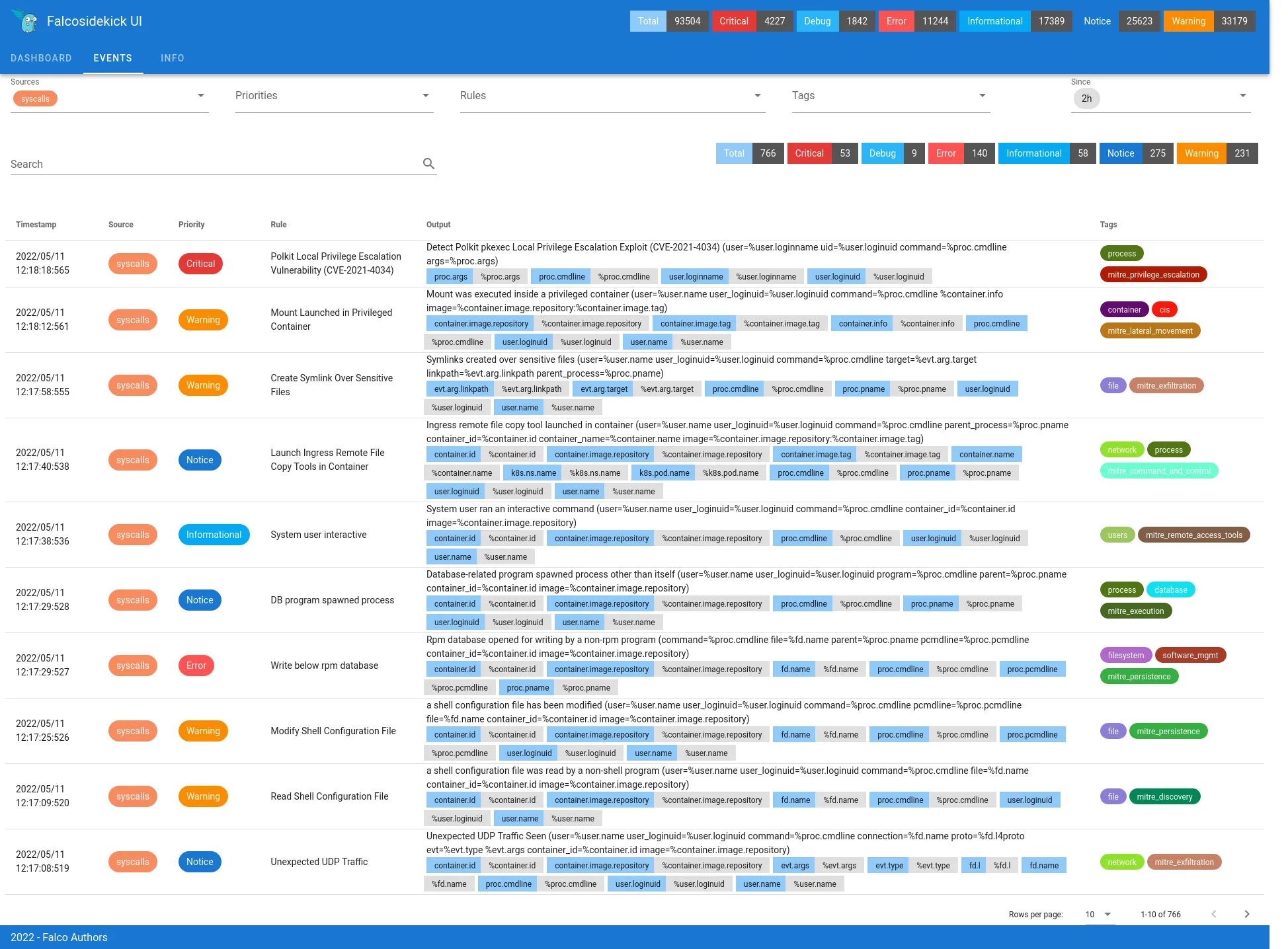
Getting Started
When to Use Falco
Falco fills the runtime detection gap that static scanners and admission controllers can’t cover. If a container gets compromised after passing all pre-deployment checks, Falco is what catches the attacker running curl inside a production pod.
It pairs well with policy engines like Kyverno or OPA Gatekeeper for admission control, and container scanners like Trivy for pre-deployment vulnerability detection. This layered approach covers the full container lifecycle.
Limitations to keep in mind: Falco requires kernel access and runs as a privileged container. Some managed Kubernetes services restrict kernel module loading.
The eBPF driver needs kernel 5.8+. Alert tuning takes time to get right in complex environments.
For a broader view of container and cloud security strategy, see our cloud infrastructure security guide. Browse other IaC security tools to compare options.
