OWASP Dependency-Track is an open-source platform for continuous component analysis across software portfolios. With 3.6k GitHub stars and 167 contributors, it is an established open-source solution for SBOM-based vulnerability management.
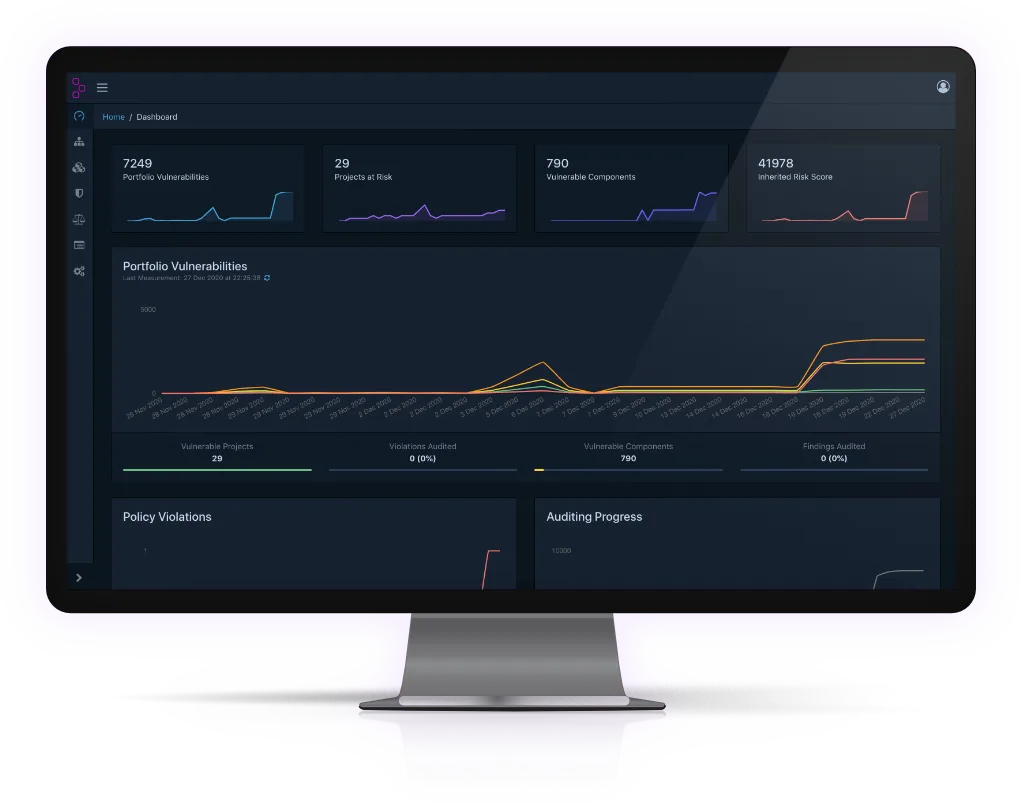
Unlike SCA scanners that run at build time and produce point-in-time reports, Dependency-Track maintains a persistent inventory of all components across your applications.
With Executive Order 14028 requiring SBOM generation for federal software, platforms that track SBOMs continuously have become increasingly relevant. When a new CVE is published, the platform immediately identifies every affected project without requiring rescans.
What is OWASP Dependency-Track?
Dependency-Track ingests SBOMs in CycloneDX or SPDX format and continuously correlates components against NVD, GitHub Advisories, Sonatype OSS Index, OSV, and optionally Snyk. It tracks component versions, licenses, and security posture across projects, giving you a unified view of organizational risk.
Key features
Vulnerability data sources
| Source | Coverage |
|---|---|
| NVD (NIST) | All CVEs in the National Vulnerability Database |
| GitHub Security Advisories | Community-reviewed advisories for GitHub ecosystems |
| Sonatype OSS Index | Java, JavaScript, .NET, and Go vulnerability data |
| OSV | Open Source Vulnerabilities across multiple ecosystems |
| Snyk (optional) | Additional vulnerability intelligence with API key |
| VulnDB (optional) | Commercial vulnerability intelligence |
Supported SBOM formats
| Format | Support |
|---|---|
| CycloneDX JSON | Full support (preferred) |
| CycloneDX XML | Full support |
| SPDX JSON | Import and export |
| SPDX tag-value | Import only |
Continuous vulnerability monitoring
Rather than scanning on-demand, Dependency-Track continuously correlates your component inventory against updated vulnerability feeds. When a new CVE affects a library you use, alerts fire automatically across all affected projects. No rescan needed.
Multi-source vulnerability intelligence
The platform aggregates data from NVD, GitHub Security Advisories, Sonatype OSS Index, OSV, and optionally Snyk. This multi-source approach catches vulnerabilities that any single database might miss.
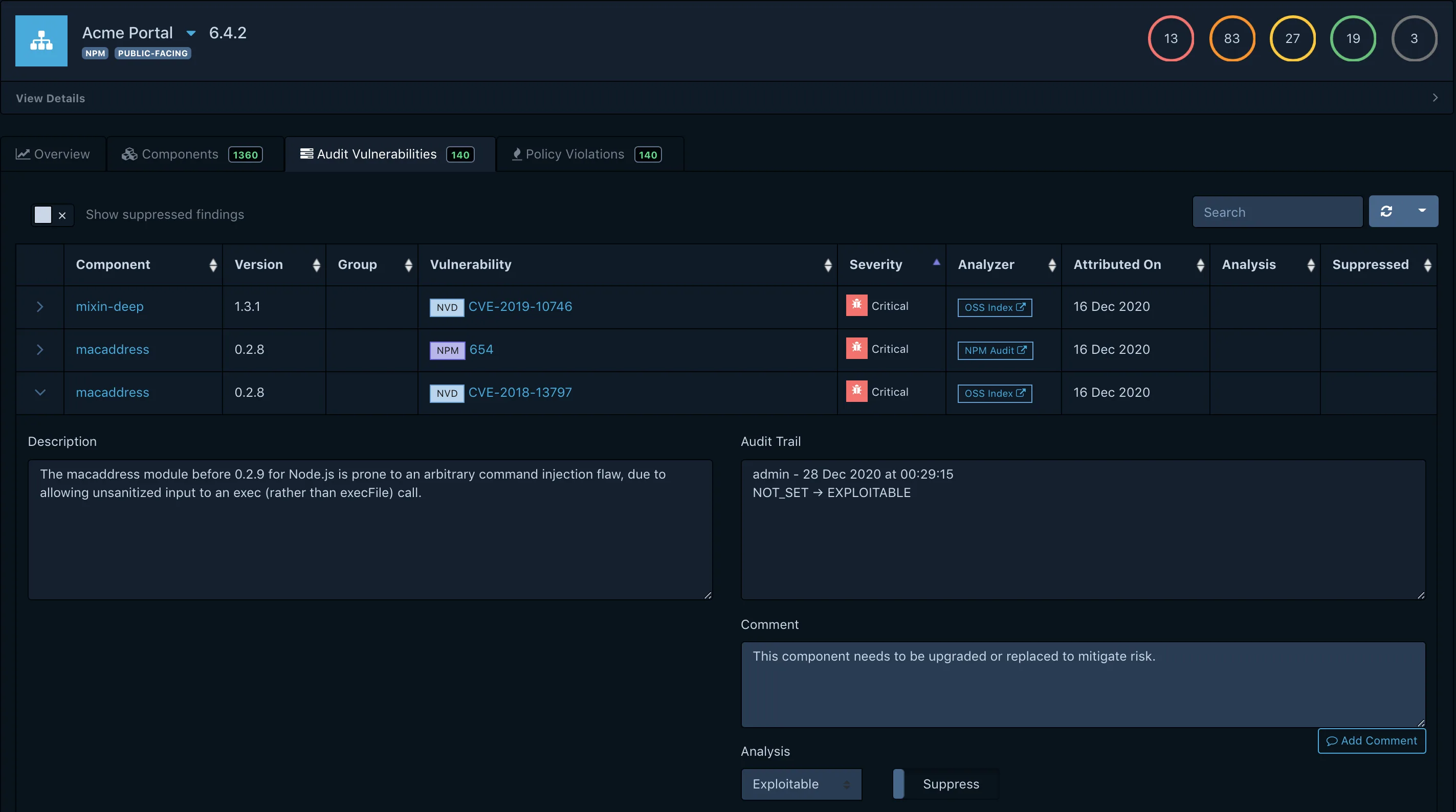
Component inventory
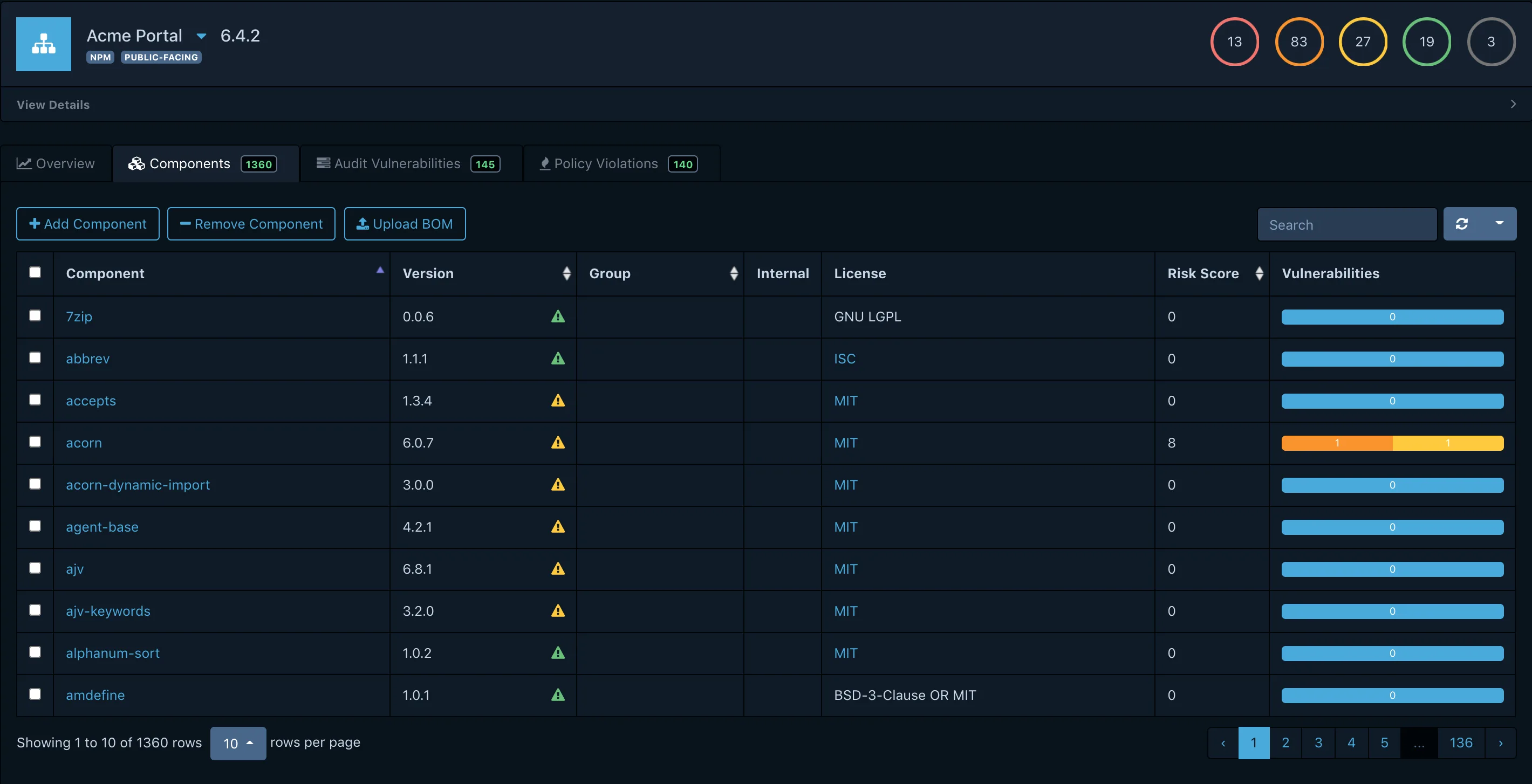
Policy engine
Define organizational policies for automated vulnerability triage. Policies can suppress false positives, escalate critical findings, or require approval for components with specific risk profiles. This reduces noise and focuses attention on actionable findings.
API-first architecture
Every feature is accessible through a REST API. Webhooks notify external systems of new vulnerabilities and policy violations.
This enables deep integration with CI/CD pipelines, ticketing systems, and custom dashboards.
Installation
Deploy Dependency-Track using Docker Compose for evaluation or production:
# Create directories
mkdir dependency-track && cd dependency-track
# Download Docker Compose file
curl -LO https://dependencytrack.org/docker-compose.yml
# Start the platform
docker compose up -d
# Access at http://localhost:8080
# Default credentials: admin / admin
For production deployments with external database:
# docker-compose.yml
version: '3.8'
services:
dtrack-api:
image: dependencytrack/apiserver:latest
environment:
- ALPINE_DATABASE_MODE=external
- ALPINE_DATABASE_URL=jdbc:postgresql://postgres:5432/dtrack
- ALPINE_DATABASE_DRIVER=org.postgresql.Driver
- ALPINE_DATABASE_USERNAME=dtrack
- ALPINE_DATABASE_PASSWORD=changeme
volumes:
- dtrack-data:/data
ports:
- "8081:8080"
dtrack-frontend:
image: dependencytrack/frontend:latest
environment:
- API_BASE_URL=http://localhost:8081
ports:
- "8080:8080"
postgres:
image: postgres:15
environment:
- POSTGRES_DB=dtrack
- POSTGRES_USER=dtrack
- POSTGRES_PASSWORD=changeme
volumes:
- postgres-data:/var/lib/postgresql/data
volumes:
dtrack-data:
postgres-data:
Uploading SBOMs
Generate SBOMs with tools like Syft, CycloneDX CLI, or build plugins:
# Generate SBOM with Syft
syft dir:./my-project -o cyclonedx-json > sbom.json
# Upload via CLI tool
dtrack-cli sbom upload \
--server http://localhost:8080 \
--api-key $DTRACK_API_KEY \
--project "My Project" \
--version "1.0.0" \
--sbom sbom.json
# Upload via curl (PUT with project name and BOM file)
curl -X PUT http://localhost:8080/api/v1/bom \
-H "X-Api-Key: $DTRACK_API_KEY" \
-F "projectName=My Project" \
-F "projectVersion=1.0.0" \
-F "autoCreate=true" \
-F "bom=@sbom.json"
CI/CD Integration
GitHub Actions
name: SBOM Upload to Dependency-Track
on:
push:
branches: [main]
jobs:
sbom-upload:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- name: Generate SBOM
uses: anchore/sbom-action@v0
with:
format: cyclonedx-json
output-file: sbom.json
- name: Upload to Dependency-Track
uses: DependencyTrack/gh-upload-sbom@v3
with:
server-url: ${{ secrets.DTRACK_URL }}
api-key: ${{ secrets.DTRACK_API_KEY }}
project-name: ${{ github.repository }}
project-version: ${{ github.sha }}
sbom-file: sbom.json
GitLab CI
stages:
- build
- security
generate-sbom:
stage: build
image: anchore/syft:latest
script:
- syft dir:. -o cyclonedx-json > sbom.json
artifacts:
paths:
- sbom.json
upload-sbom:
stage: security
image: curlimages/curl:latest
script:
- |
curl -X PUT "${DTRACK_URL}/api/v1/bom" \
-H "X-Api-Key: ${DTRACK_API_KEY}" \
-F "projectName=${CI_PROJECT_NAME}" \
-F "projectVersion=${CI_COMMIT_SHORT_SHA}" \
-F "autoCreate=true" \
-F "bom=@sbom.json"
dependencies:
- generate-sbom
Jenkins Pipeline
pipeline {
agent any
stages {
stage('Generate SBOM') {
steps {
sh 'syft dir:. -o cyclonedx-json > sbom.json'
}
}
stage('Upload to Dependency-Track') {
steps {
dependencyTrackPublisher(
artifact: 'sbom.json',
projectName: 'My Project',
projectVersion: "${BUILD_NUMBER}",
synchronous: true
)
}
}
}
}
Setup
curl -LO https://dependencytrack.org/docker-compose.yml && docker compose up -d. Access the UI at http://localhost:8080.dtrack-cli tool. Set up CI/CD integration to upload automatically on each build.When to use Dependency-Track
Dependency-Track is the right choice for organizations managing multiple applications that need centralized, continuous visibility into component risk.
Strengths:
- Continuous monitoring catches new CVEs without rescans
- SBOM-first approach with CycloneDX and SPDX support
- Multi-source vulnerability intelligence (NVD, GitHub, OSS Index, OSV)
- Portfolio-wide risk tracking and policy engine
- Free and open-source (Apache 2.0)
Limitations:
- Not a scanner itself; requires external SBOM generation
- Requires infrastructure to host (Docker, Kubernetes)
- No automated fix PRs or remediation workflows
How it compares:
| vs. | Key difference |
|---|---|
| OWASP Dependency-Check | Dependency-Check is a point-in-time scanner. Dependency-Track is a continuous monitoring platform. Many teams use both together. |
| DefectDojo | DefectDojo aggregates findings from multiple security tools. Dependency-Track focuses specifically on component/SBOM tracking with deeper vulnerability correlation. |
| Grype | Grype is a fast CLI scanner for CI/CD. Dependency-Track adds the persistent tracking layer that point-in-time scanners lack. |
See also our guides on What is SCA? and software supply chain security.