Contrast Security is an application security platform that uses runtime instrumentation to detect and block vulnerabilities. The platform combines IAST, RASP, SAST, and SCA capabilities under a unified developer-focused interface.
Unlike traditional scanners that analyze code statically or test from the outside, Contrast instruments applications with agents that observe code execution in real time. The company was recognized as a Visionary in the 2025 Gartner Magic Quadrant for Application Security Testing.
Platform components
Contrast Security consists of four main products that share a common instrumentation agent and dashboard:
Contrast Assess — Interactive Application Security Testing (IAST) that finds vulnerabilities in running code during development and QA testing.
Contrast Protect — Runtime Application Self-Protection (RASP) that blocks attacks in production without code changes.
Contrast Scan — Static Application Security Testing (SAST) built for CI/CD pipelines with fast scan times and low false positive rates.
Contrast SCA — Software Composition Analysis that identifies vulnerable open-source libraries and prioritizes fixes based on runtime usage.
How Contrast Security works
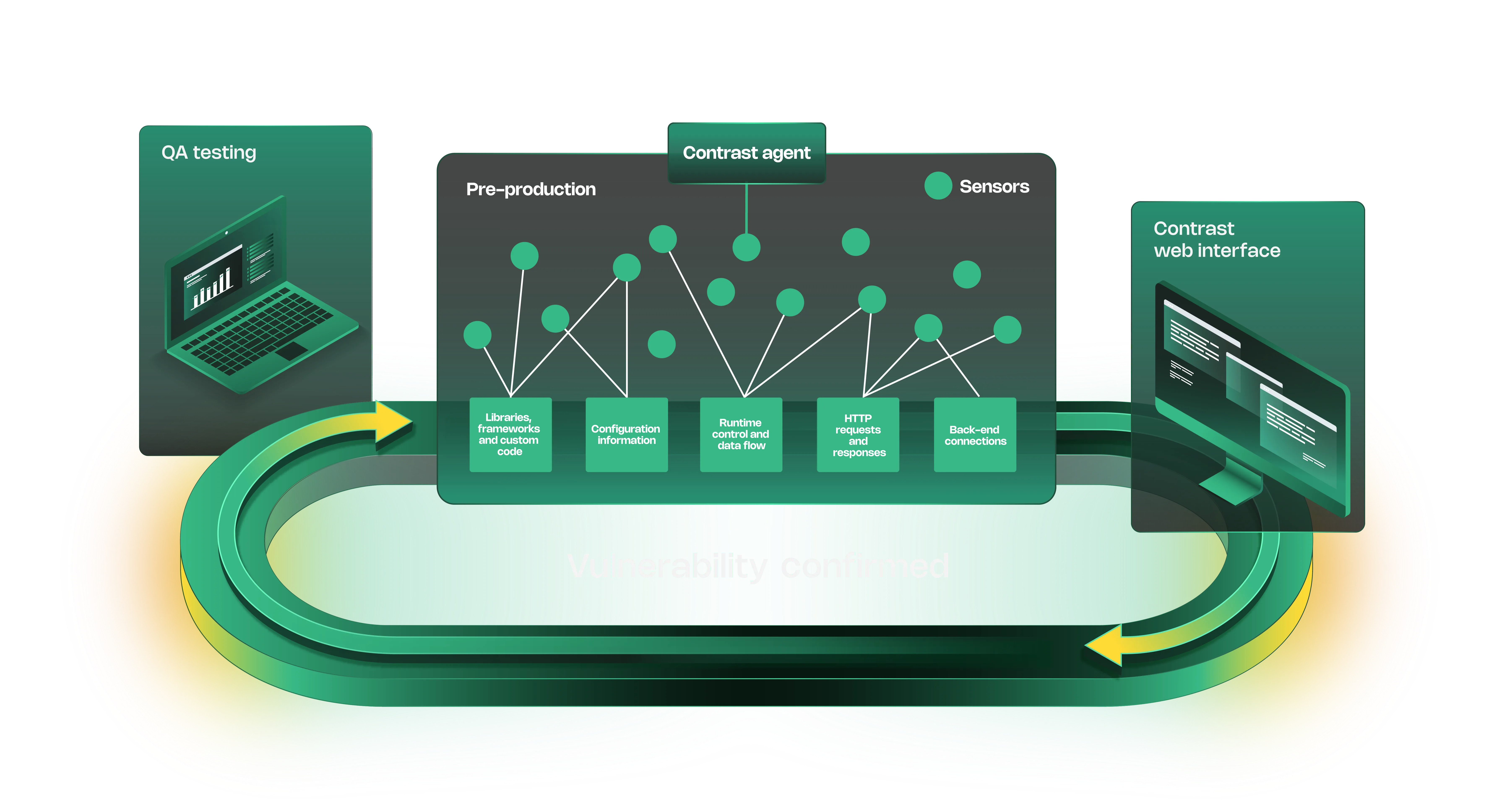
Contrast Security instruments applications with language-specific agents (Java, .NET, Node.js, Python, Ruby, Go). The agent monitors code execution during normal application usage, automated tests, or production traffic.
When vulnerable code paths execute — like unsanitized user input reaching a SQL query — the agent reports the vulnerability with full context: stack trace, data flow, affected endpoints, and fix guidance.
This runtime approach identifies vulnerabilities that exist in actual code paths rather than every possible vulnerability in the codebase. Unused functions and dead code don’t generate findings.
Contrast Assess (IAST)
Contrast Assess finds vulnerabilities during development and QA testing. Install the agent, run automated tests or manually use the application, and Assess reports security issues it observes.
The IAST engine traces data from sources (user input, file reads, external APIs) through the application to sinks (database queries, OS commands, file writes). When tainted data reaches a dangerous operation without proper validation, Assess reports the vulnerability.
Supported languages: Java, .NET (Framework & Core), Node.js, Python, Ruby, Go.
Detected vulnerabilities: SQL injection, XSS, command injection, path traversal, XXE, insecure deserialization, weak cryptography, LDAP injection.
Contrast Protect (RASP)
Contrast Protect blocks attacks in production by monitoring requests and blocking exploitation attempts. The same instrumentation agent used for IAST adds runtime protection.
When an attack is detected — like SQL injection in a query parameter — Protect blocks the request and logs the event. No code changes required.
The protection runs inside the application, not at the network perimeter.
Performance impact is typically under 5% overhead. Protect runs alongside existing WAF and network security tools.
Contrast Scan (SAST)
Contrast Scan analyzes source code for security vulnerabilities without requiring compilation or execution. Built for CI/CD pipelines, scans complete in minutes rather than hours.
Scan focuses on accuracy to reduce false positives. It integrates into pull requests, shows findings inline in code, and provides fix suggestions.
Supported languages: Java, .NET, JavaScript/TypeScript, Python, Ruby, Go, PHP.
Contrast SCA
Contrast SCA identifies vulnerable open-source libraries in application dependencies. It monitors which libraries are actually loaded and executed at runtime, not just listed in dependency manifests.
This runtime analysis prioritizes vulnerabilities in libraries your application uses. Dependencies listed in package.json but never loaded don’t trigger alerts.
SCA detects vulnerable versions, license compliance issues, and outdated dependencies. Integrates with Dependabot, Snyk, and other supply chain tools for unified visibility.
Key features
| Feature | Details |
|---|---|
| Instrumentation | Java, .NET (Framework/Core), Node.js, Python, Ruby, Go |
| IAST (Assess) | Runtime vulnerability detection during testing with data flow analysis |
| RASP (Protect) | Production attack blocking with sub-5% overhead |
| SAST (Scan) | Fast pipeline-native source code scanning |
| SCA | Runtime library analysis and vulnerability prioritization |
| Deployment | On-premises, SaaS, hybrid, air-gapped environments |
| Integrations | IDE plugins, CI/CD (GitHub Actions, Jenkins, GitLab), Jira, Slack |
| Compliance | OWASP Top 10, CWE coverage, PCI-DSS, HIPAA, SOC 2 support |
Getting started
CI/CD integration
Contrast Scan integrates into CI/CD pipelines as a CLI tool. Run scans in GitHub Actions, GitLab CI, Jenkins, or any pipeline that executes shell commands.
# GitHub Actions example
- name: Contrast Scan
run: |
contrast scan \
--file target/app.jar \
--api-key ${{ secrets.CONTRAST_API_KEY }} \
--authorization ${{ secrets.CONTRAST_AUTH }} \
--organization-id ${{ secrets.CONTRAST_ORG_ID }}
The CLI exits with non-zero status when vulnerabilities above a severity threshold are detected. This fails builds before vulnerable code merges.
When to use Contrast Security
Contrast Security works well for teams that want runtime-based security testing with low false positives. The instrumentation approach reduces alert fatigue by focusing on vulnerabilities in code paths that actually execute.
Organizations running Java, .NET, or Node.js applications benefit most from the runtime agent support. Teams that already use automated testing get immediate value from IAST without changing their test process.
The platform suits both development (Assess, Scan, SCA) and production (Protect) use cases. Running IAST during QA and RASP in production provides security coverage across the lifecycle.
For teams preferring non-instrumentation approaches, Snyk Code offers IDE-integrated SAST and Semgrep provides custom rule-based static analysis. For web application scanning without agent installation, Invicti and Burp Suite provide DAST capabilities.
Browse other IAST tools and RASP tools to compare runtime security options.